Difference between revisions of "Setting up SSL certificates from Self Service Portal"
| (9 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
= Overview | = Overview= | ||
<p> | |||
''HTTPS-aware'' applications such as Internet Browsers, implement '''SSL/TLS''' protocols to prevent inadvertent communication with a malafide web service.<br />The SSL / TLS protocols enable applications to verify identity of the remote web services, and appropriately encrypt the entire communication preventing any third-party to eavesdrop.<br> | |||
In response to the SSL Handshake initiated by the client application, the remote web service submits identification using a '''Digital Server (SSL/TLS) Certificate'''.<br> | |||
The client application maintains stores of CA certificates representing various '''''Trusted Root Certification Authority'''''.<br> | |||
Unless explicitly ''trusted'', the client application checks if the server certificate is signed by a ''Trusted Root CA''.<br> | |||
The Trusted Root CA binds the server certificate to a set of FQDNs, and ensures each signed certificate bears a unique ''serial number''.<br /> | |||
Post verification the client proceeds with normal HTTP Protocol, but the communication is encrypted based on the parameters agreed during the SSL handshake, and the server certificate.The communication is thus ''opaque'' and cannot be inspected or modified by a third-party. | |||
</p> | |||
<p> | |||
To inspect inspect and / modify the communication between a client and server, a proxy server ''terminates'' connections.<br> | |||
For handling HTTPS traffic it must additionally perform ''SSL Termination''.<br> | |||
This requires the proxy server to provide an SSL Certificate for the web service requested by the client.<br> | |||
For seamless user experience, this SSL certificate must be signed by a ''Trusted Root CA''.<br> | |||
Enterprises therefore ensure a Trusted Root CA is installed in the ''Trusted Root CA Store'' of the sanctioned web applications, such as Internet Browsers.<br> | |||
The proxy server is provided this Trusted Root CA, along with the associated ''Private Key''.<br> | |||
The proxy server then produces the required SSL certificates for any web service and signs it using the provided ''Certificate-Key pair''.<br> | |||
Enterprises that require multiple instances of proxy services to handle large traffic volumes, or geographic spread.<br> | |||
The deployment must also guarantee each certificate thus created by proxy servers have a distinct serial number. | |||
</p> | |||
<p> | |||
The '''Self-Service Portal''' for managing your SafeSquid deployments, facilitates easy creation of Trusted Root CA Certificates.<br> | |||
You would be required to then share the CA certificate with your enterprise users, or push it via Group Policies, if you have a Microsoft Domain Network.<br> | |||
You may also ''import'' an SSL CA Certificate, provided by your existing ''Enterprise CA Infrastructure''.<br> | |||
In such case you would not be required to push a Trusted Root CA Certificate.<br> | |||
All SafeSquid instances deployed by you that share the same ''Product Activation Key'', shall automatically download the Trusted Root CA certificate.<br> | |||
Each SafeSquid instance shall then produce a sub-CA certificate-key pair, to sign the SSL Certificates for requested web services.<br> | |||
This mechanism ensures each SSL certificate bears a unique serial number, and signature, but only one Trusted Root CA Certificate is to be shared across client applications.<br> | |||
All Certificate-Key pairs are ''passphrase'' protected to prevent misuse. | |||
</p> | |||
__TOC__ | |||
{| style="width: 100%" | |||
{| style="width: 100%" cellspacing="1" cellpadding="1" border="0" | |||
|- | |- | ||
| style="width: 940px" | | | style="width: 940px" | | ||
= [[Access_The_Self_Service_Portal|Access the Self Service Portal]] = | =[[Access_The_Self_Service_Portal|Access the Self Service Portal]]= | ||
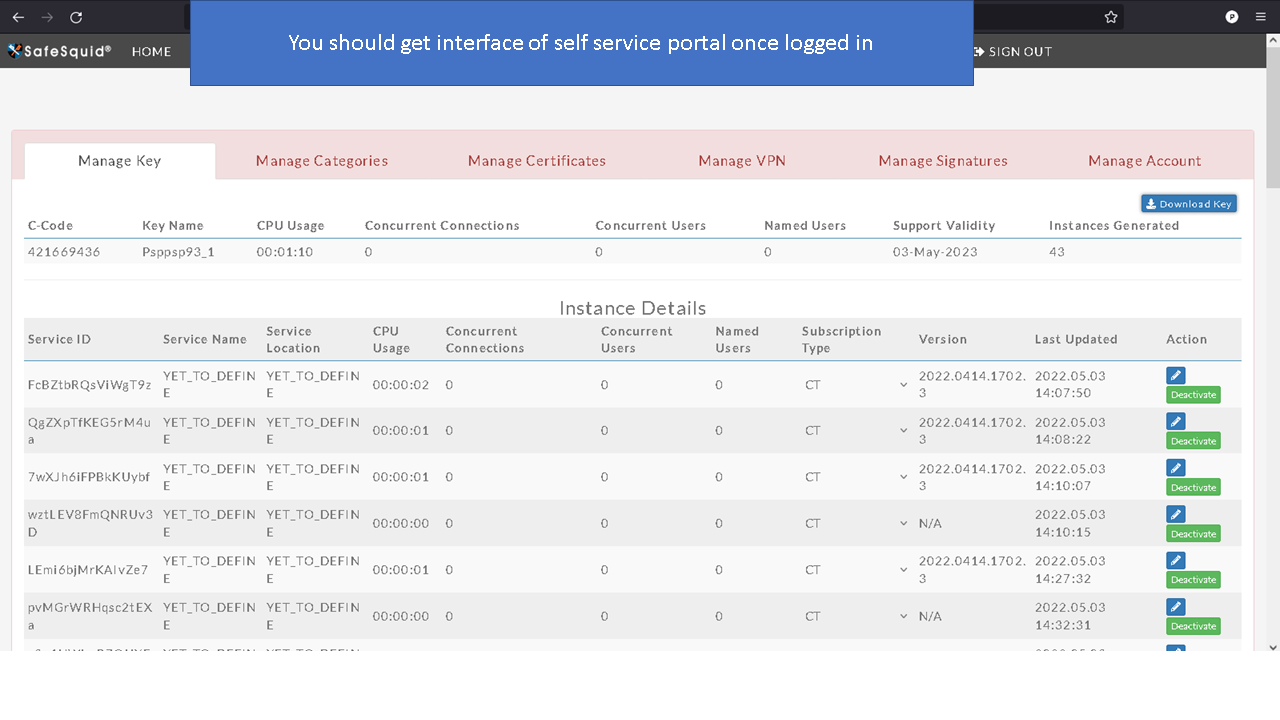
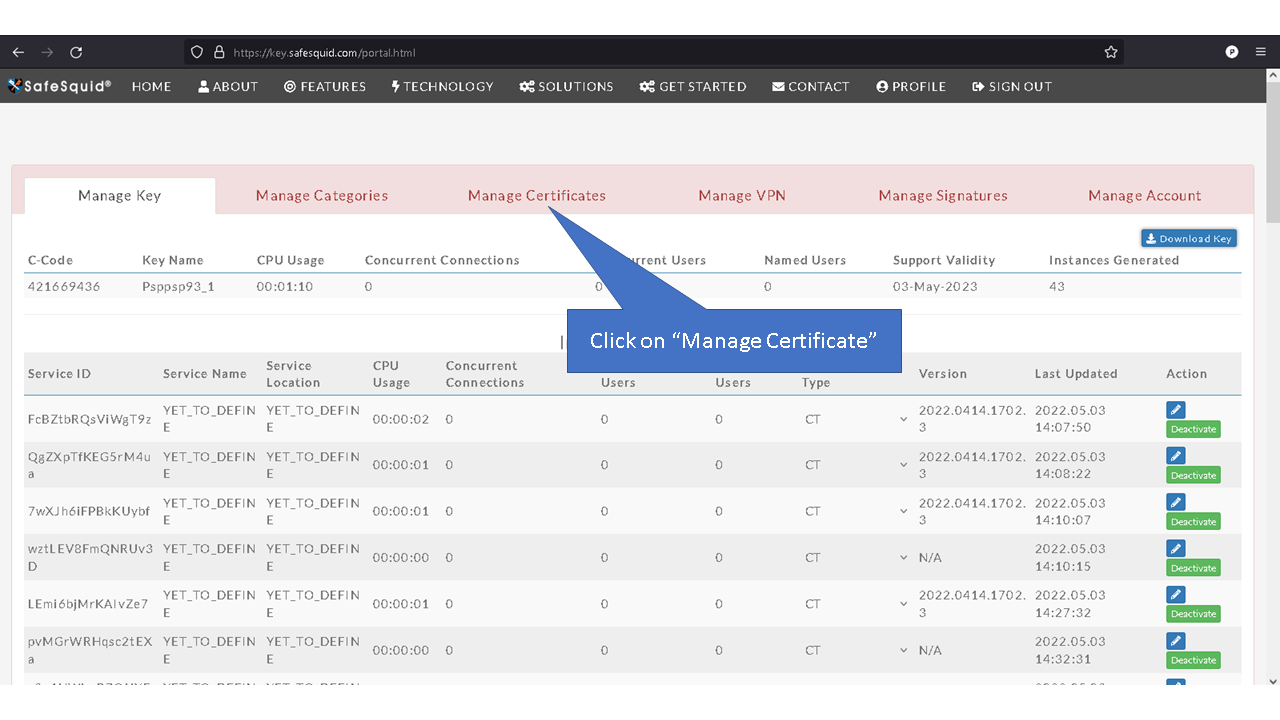
You can access the Self Service Portal from https://key.safesquid.com | You can access the Self Service Portal from https://key.safesquid.com | ||
Login to your SafeSquid Self Service Portal https://key.safesquid.com account to generate SSL certificate as generation of certificate cannot be done via SafeSquid's web interface http://safesquid.cfg/ | |||
| | [[File:Slide1-SSLGen.png|left]] | ||
[[File:Slide2-SSLGen.png|left]] | |||
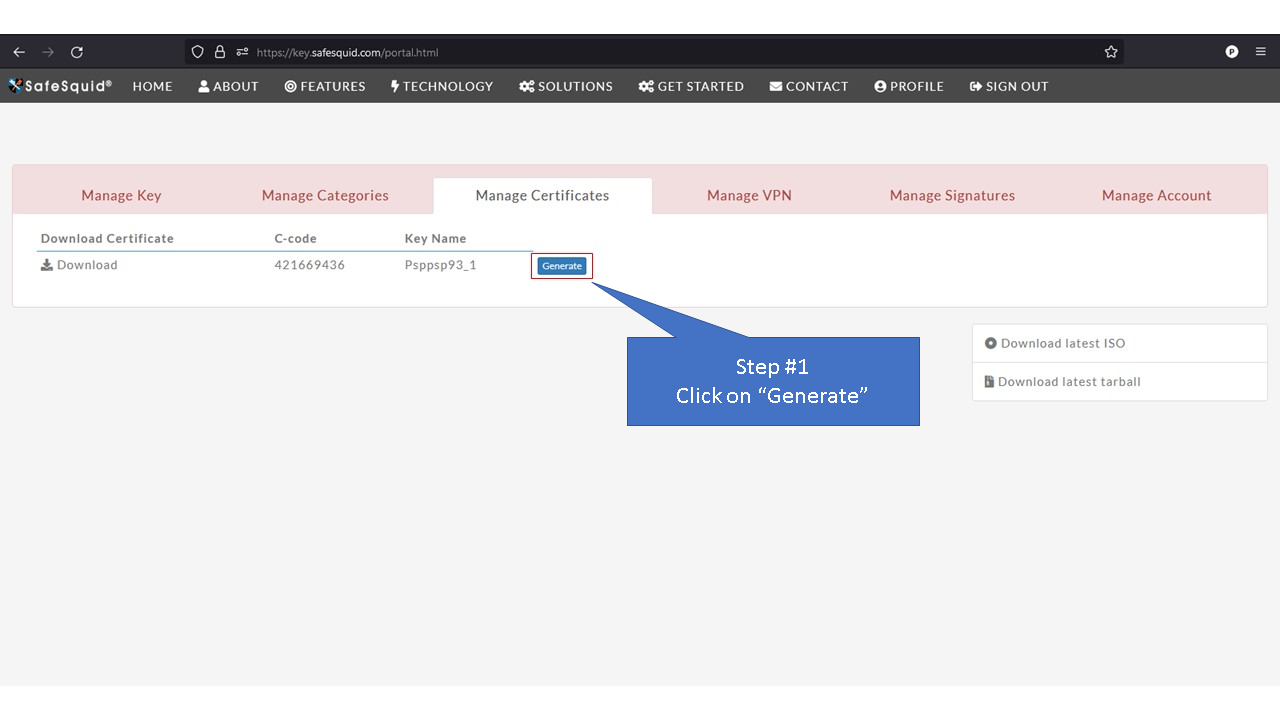
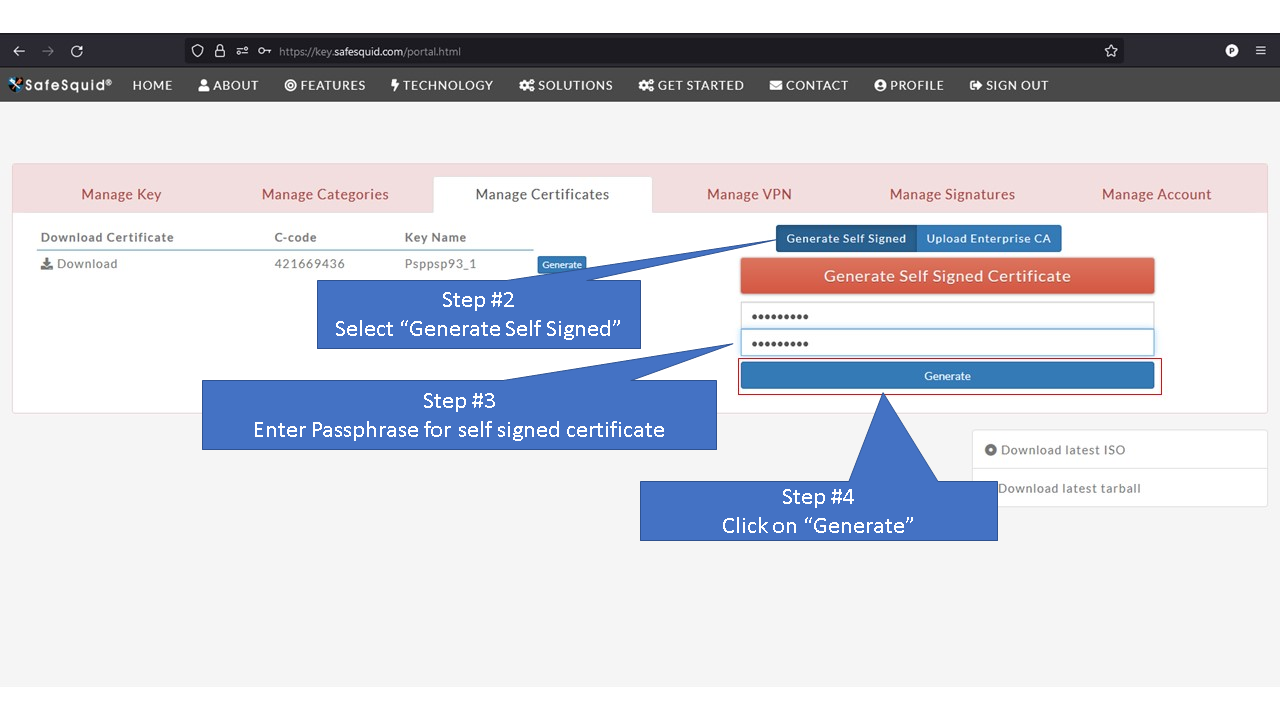
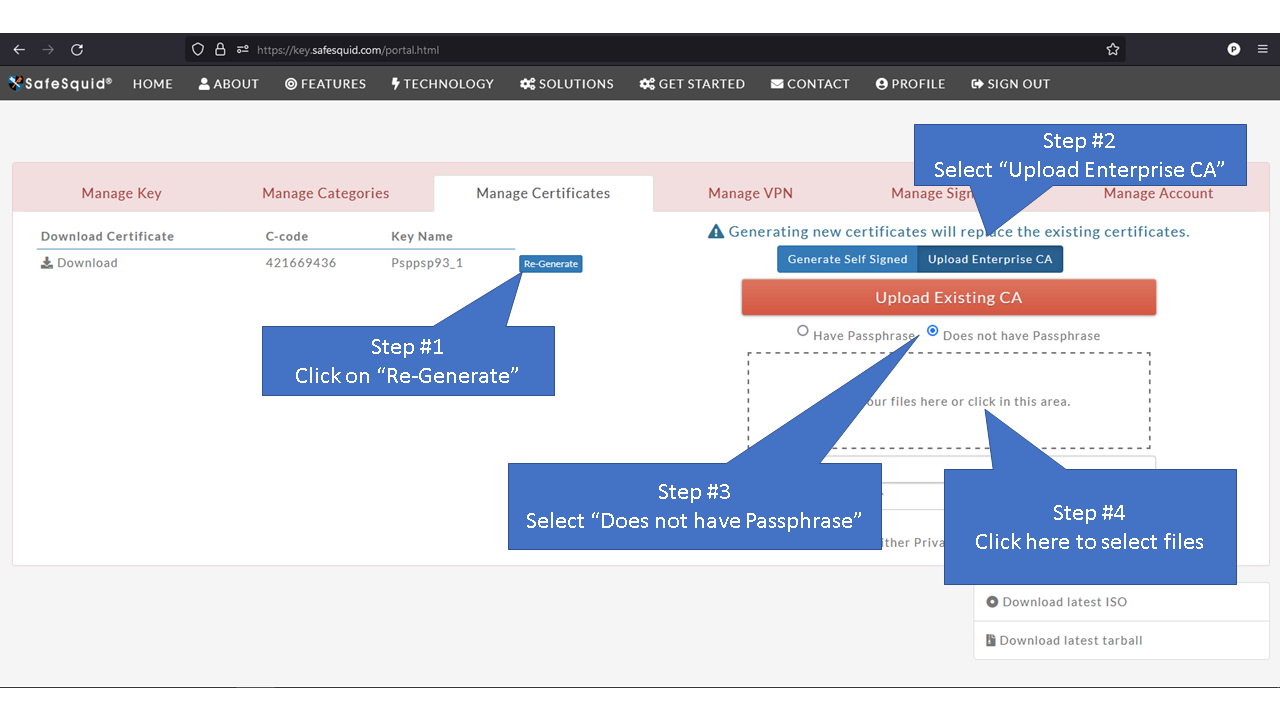
= Generate Self Signed Certificate = | |||
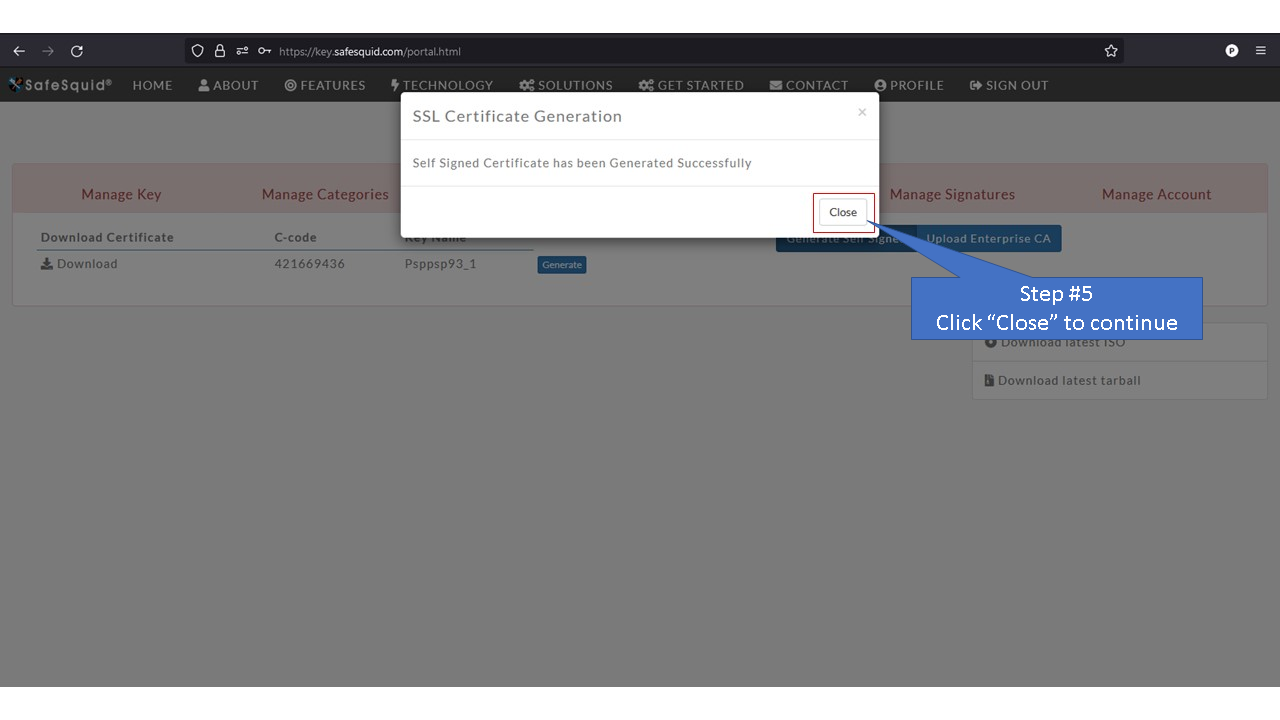
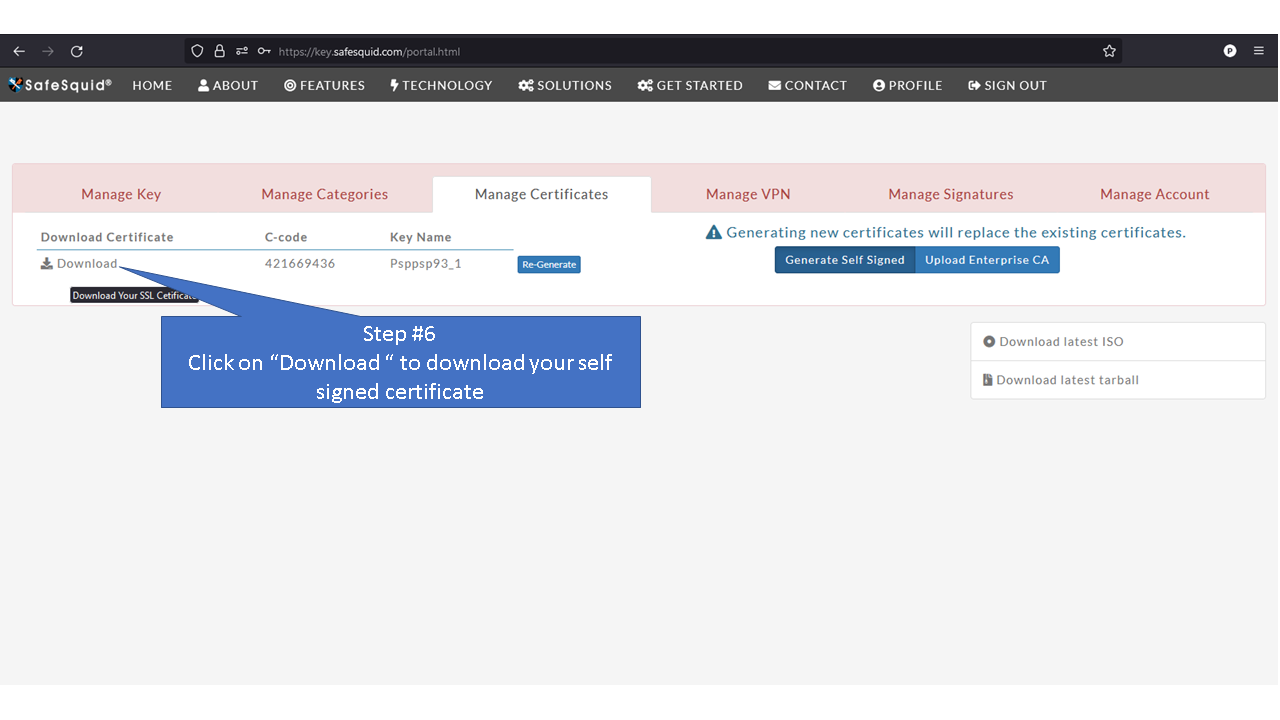
'''Note:''' When you see "Generate" button it means that SafeSquid's SSL certificate has not been generated yet. | |||
[[File:Slide3-SSLGen.png|left]] | |||
[[File:Slide4-SSLGen.png|right]] | |||
[[File:Slide5-SSLGen.png|left]] | |||
[[File:Slide6-SSLGen.png|left]] | |||
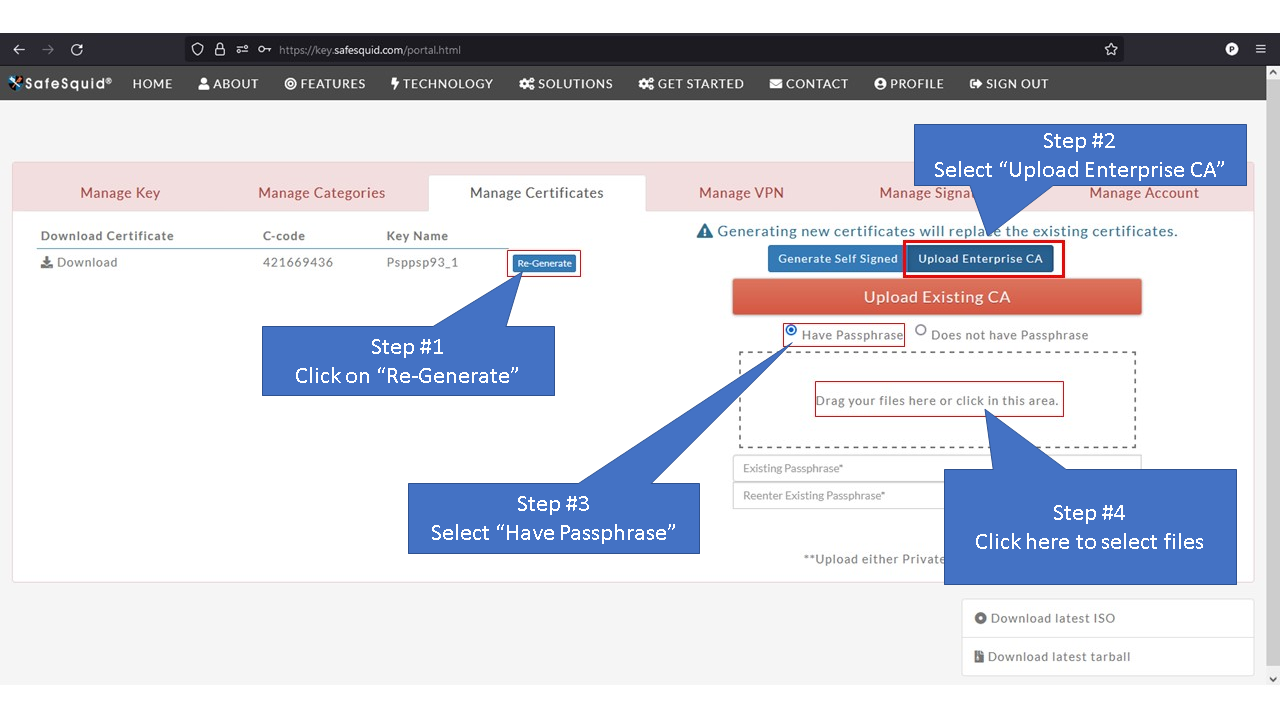
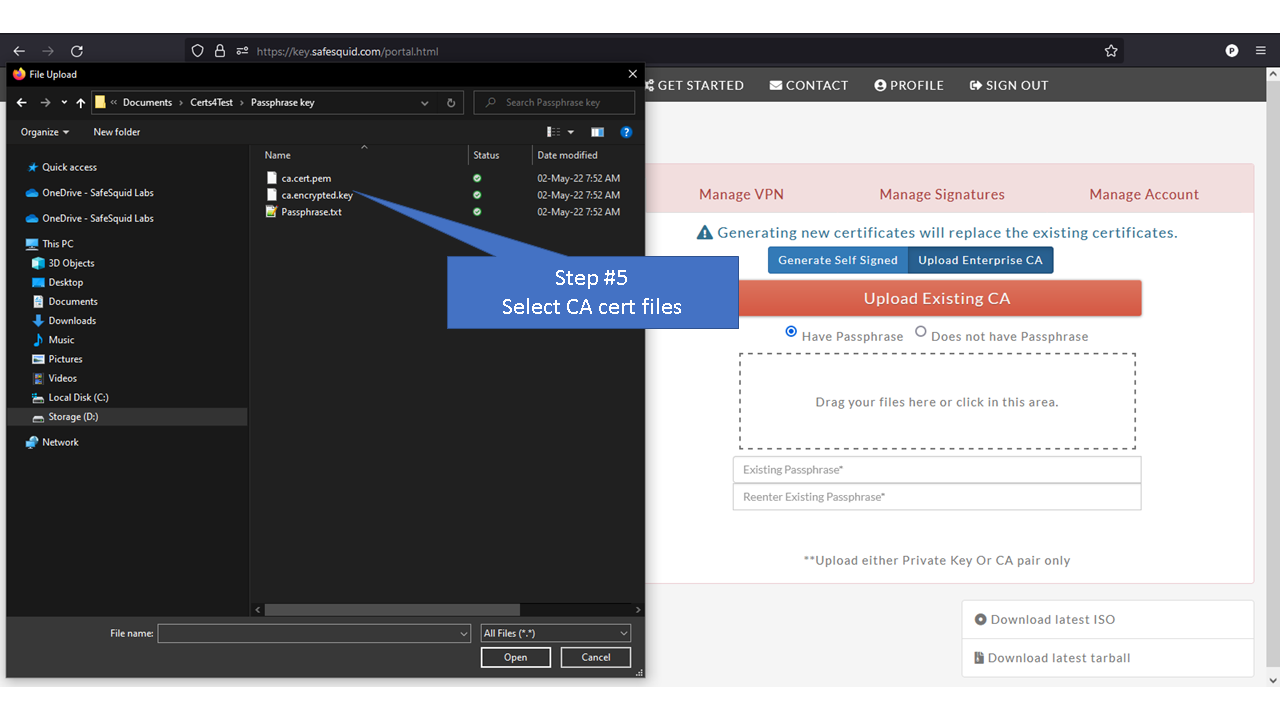
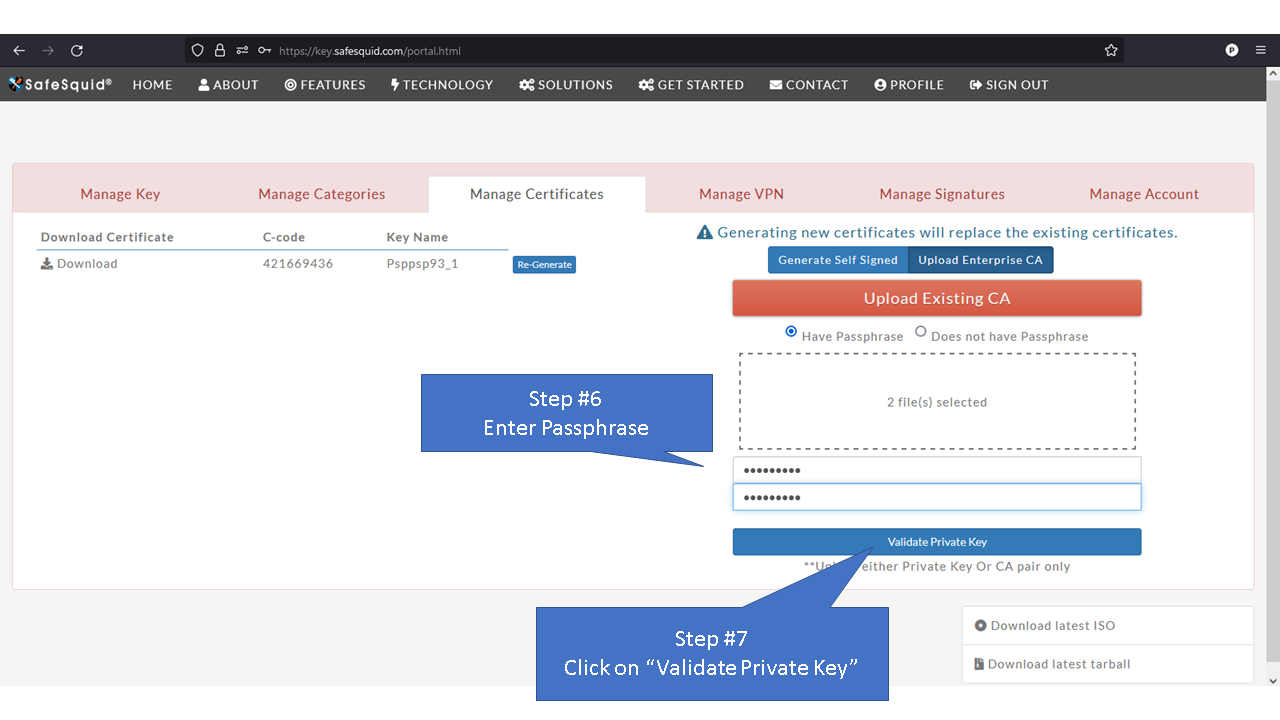
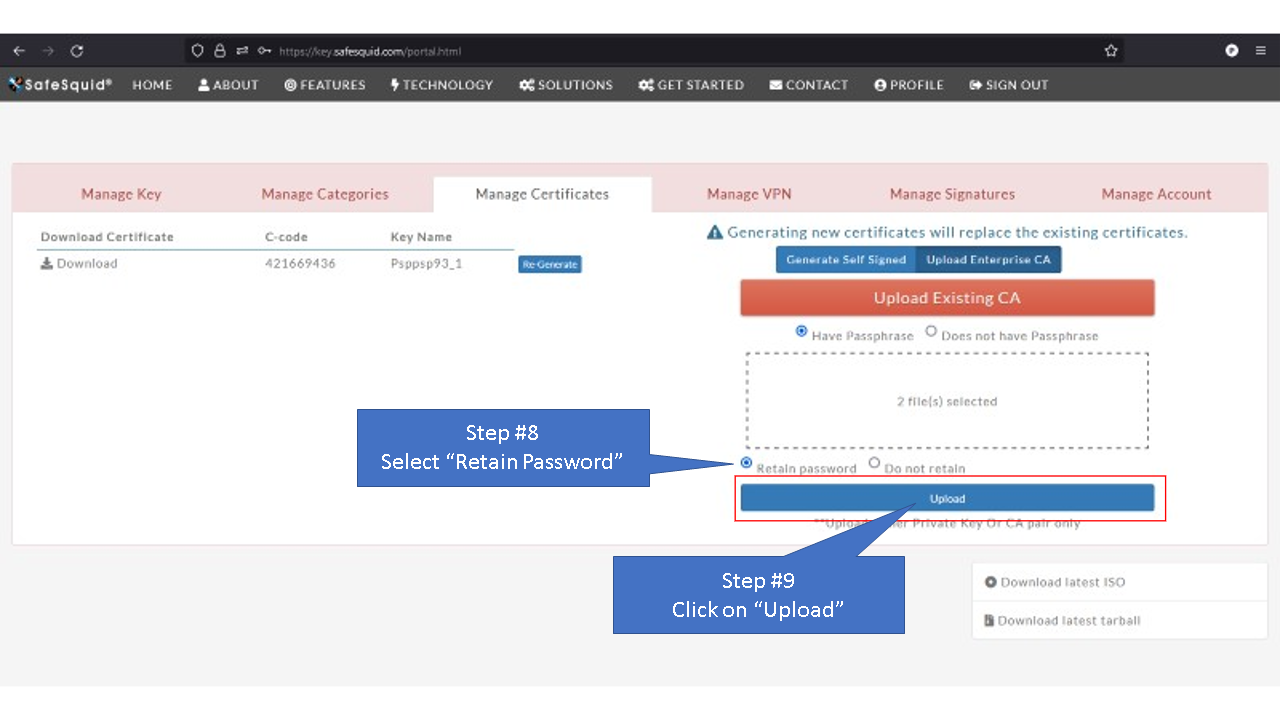
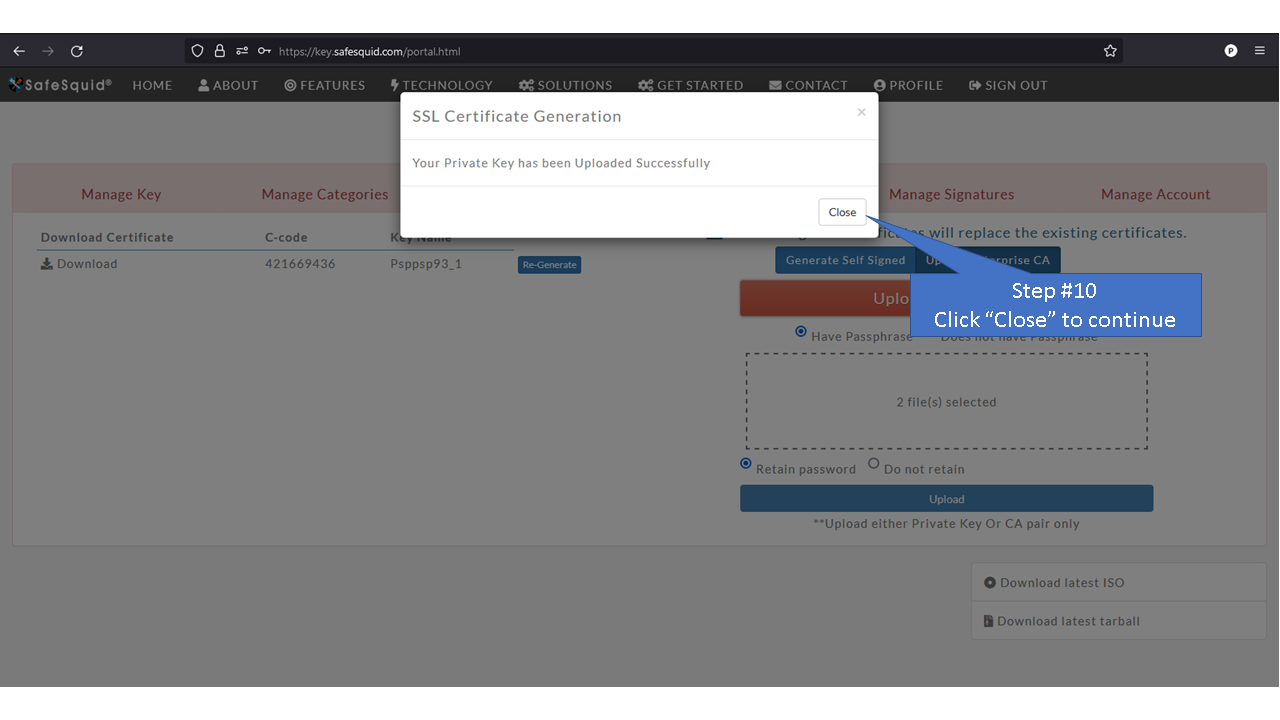
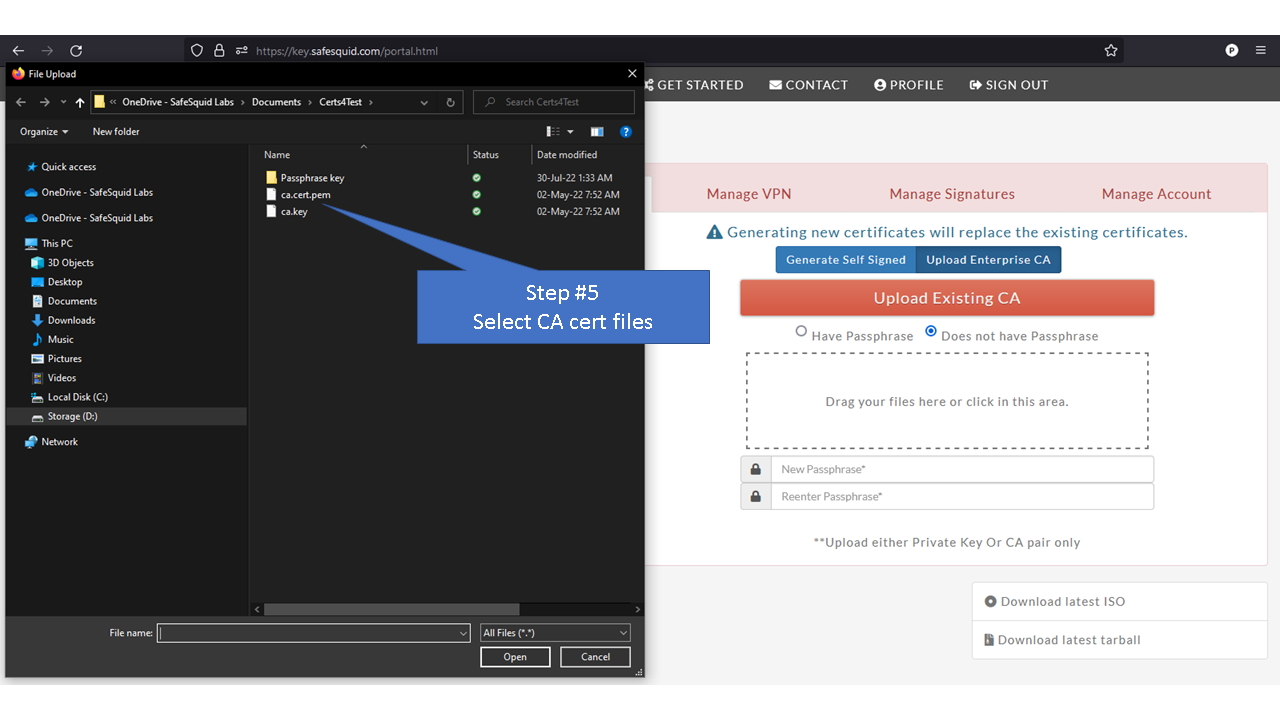
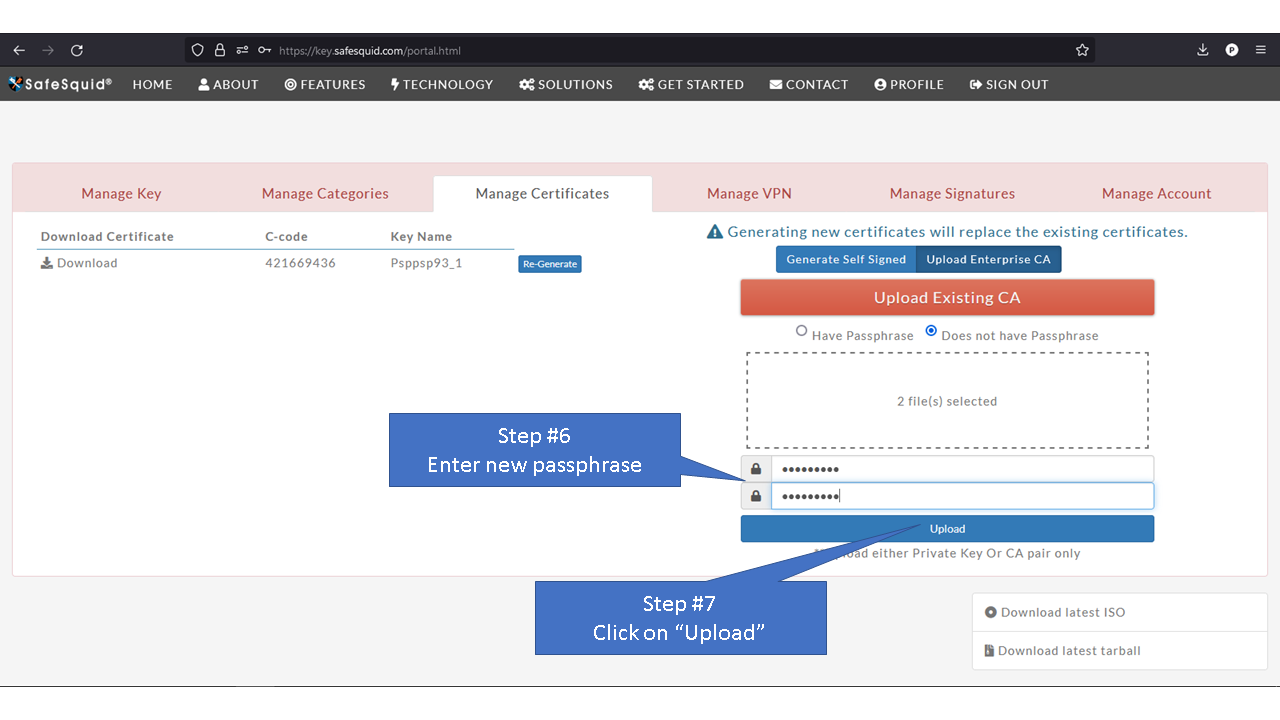
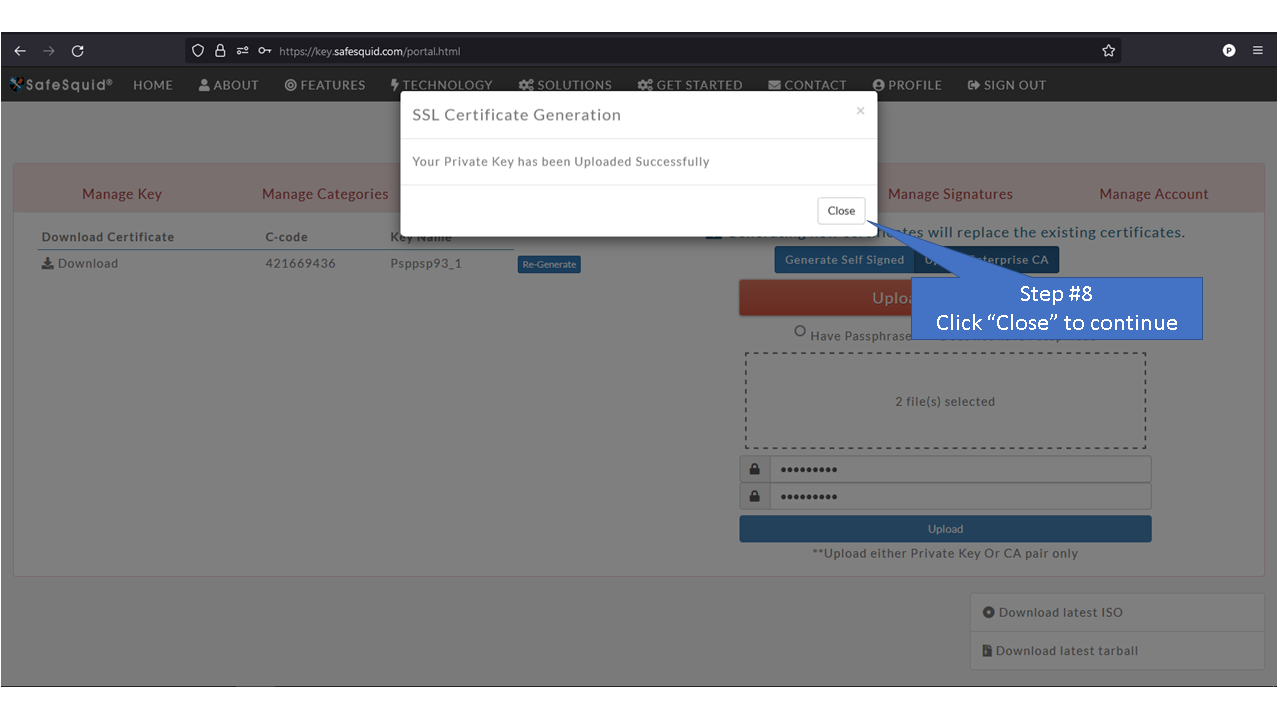
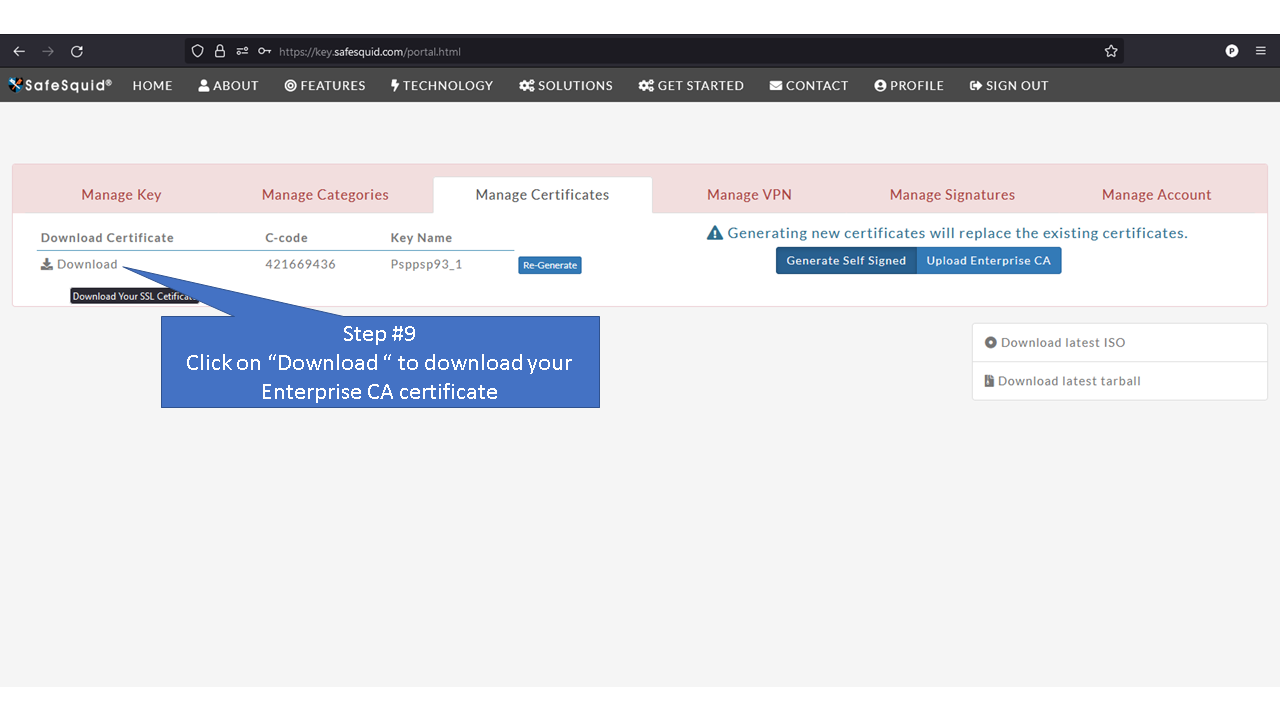
[[File: | =Using Enterprise CA Certificate With Passphrase= | ||
[[File:Slide7-SSLGen.png|left]] | |||
[[File:Slide8-SSLGen.png|left]] | |||
[[File:Slide9-SSLGen.png|left]] | |||
[[File:Slide10-SSLGen.png|left]] | |||
[[File:Slide11-SSLGen.png|left]] | |||
[[File:Slide6-SSLGen.png|left]] | |||
=Using Enterprise CA Certificate Without Passphrase= | |||
| | [[File:Slide13-SSLGen.png|left]] | ||
[[File:Slide14-SSLGen.png|left]] | |||
[[File: | [[File:Slide15-SSLGen.png|left]] | ||
[[File:Slide16-SSLGen.png|left]] | |||
[[File:Slide17-SSLGen.png|left]] | |||
|} | |||
[[Category:Product Activation]] | |||
[[ | |||
Latest revision as of 17:28, 3 October 2023
Overview
HTTPS-aware applications such as Internet Browsers, implement SSL/TLS protocols to prevent inadvertent communication with a malafide web service.
The SSL / TLS protocols enable applications to verify identity of the remote web services, and appropriately encrypt the entire communication preventing any third-party to eavesdrop.
In response to the SSL Handshake initiated by the client application, the remote web service submits identification using a Digital Server (SSL/TLS) Certificate.
The client application maintains stores of CA certificates representing various Trusted Root Certification Authority.
Unless explicitly trusted, the client application checks if the server certificate is signed by a Trusted Root CA.
The Trusted Root CA binds the server certificate to a set of FQDNs, and ensures each signed certificate bears a unique serial number.
Post verification the client proceeds with normal HTTP Protocol, but the communication is encrypted based on the parameters agreed during the SSL handshake, and the server certificate.The communication is thus opaque and cannot be inspected or modified by a third-party.
To inspect inspect and / modify the communication between a client and server, a proxy server terminates connections.
For handling HTTPS traffic it must additionally perform SSL Termination.
This requires the proxy server to provide an SSL Certificate for the web service requested by the client.
For seamless user experience, this SSL certificate must be signed by a Trusted Root CA.
Enterprises therefore ensure a Trusted Root CA is installed in the Trusted Root CA Store of the sanctioned web applications, such as Internet Browsers.
The proxy server is provided this Trusted Root CA, along with the associated Private Key.
The proxy server then produces the required SSL certificates for any web service and signs it using the provided Certificate-Key pair.
Enterprises that require multiple instances of proxy services to handle large traffic volumes, or geographic spread.
The deployment must also guarantee each certificate thus created by proxy servers have a distinct serial number.
The Self-Service Portal for managing your SafeSquid deployments, facilitates easy creation of Trusted Root CA Certificates.
You would be required to then share the CA certificate with your enterprise users, or push it via Group Policies, if you have a Microsoft Domain Network.
You may also import an SSL CA Certificate, provided by your existing Enterprise CA Infrastructure.
In such case you would not be required to push a Trusted Root CA Certificate.
All SafeSquid instances deployed by you that share the same Product Activation Key, shall automatically download the Trusted Root CA certificate.
Each SafeSquid instance shall then produce a sub-CA certificate-key pair, to sign the SSL Certificates for requested web services.
This mechanism ensures each SSL certificate bears a unique serial number, and signature, but only one Trusted Root CA Certificate is to be shared across client applications.
All Certificate-Key pairs are passphrase protected to prevent misuse.
Access the Self Service PortalYou can access the Self Service Portal from https://key.safesquid.com Login to your SafeSquid Self Service Portal https://key.safesquid.com account to generate SSL certificate as generation of certificate cannot be done via SafeSquid's web interface http://safesquid.cfg/ Generate Self Signed CertificateNote: When you see "Generate" button it means that SafeSquid's SSL certificate has not been generated yet. Using Enterprise CA Certificate With PassphraseUsing Enterprise CA Certificate Without Passphrase |