Header filter
Overview
Here, you can control how the SafeSquid edits the HTTP header messages that pass between your browser and the Internet.
You can Increase internet usage privacy levels.
Control the client requests and web server responses.
You can add, delete or modify the Request and Response headers based on their content.
Apart from allowing or denying request or response headers, you can also use Insert sub-section to add a new header or to modify them.
This section analyzes:
Request header patterns that are passed from browsers to webservers.
Response header patterns that are coming from webservers to clients.
Global
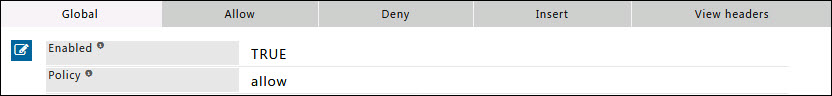
Enabled
Enable or Disable header filter section.
- TRUE : Enable header filter section.
- FALSE : Disable header filter section.
Policy
Select the default action to take, when no matching entry for a requested header is found.
- ALLOW : Allow everything Except rules defined under Deny subsection.
- DENY : Deny everything Except rules defined under Allow subsection.
Allow
When the Policy is Deny, rules defined under this sub-section, are exclusively allowed access.
Here you can add a new allow entry, that would explicitly result in acceptance or allowance of header filter to all or specific set of conditions.
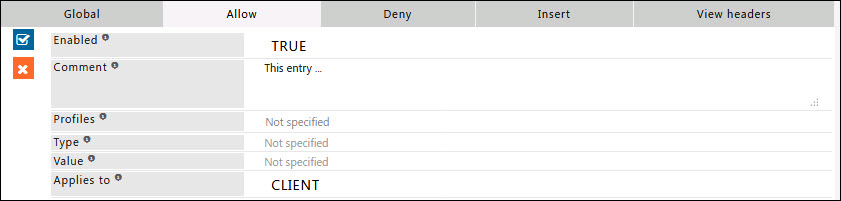
Enabled
Enable or Disable this entry
- TRUE : Enable this entry
- FALSE : Disable this entry
Comment
For documentation, and future references, explainthe relevance of this entry with your policies.
Profiles
Specify the Profiles applicable for this entry.
This entry will be applicable only if the connection has any one of the specified profiles.
Leave it Blank, to apply for all connections irrespective of any applied profile.
To avoid application to a connection that has a profile, use negated profile (!profile).
Type
A regular expression matching the header type to which this entry applies to.
Headers are in the form of type and value.
Leave blank to Match everything.
Example : X-GoogApps-Allowed-Domains.
Value
A regular expression matching the header value's this entry applies to leave blank to match everything.
Leave blank to Match everything.
Example : text/html.
Applies to
This option is to select whether this entry applies to the server header, client header, or both.
- CLIENT : This entry will be applied only for request headers, sent by the client.
- SERVER : This entry will be applied only for response headers, sent by the server.
Deny
When the Policy is Allow, rules defined under this sub-section, are denied access exclusively.
Here you can add a new 'allow' entry, that would explicitly result in blocking or denial the header filter to all or specific set of conditions.
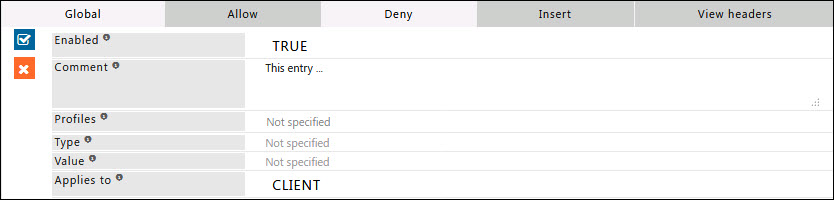
Enabled
Enable or Disable this entry
- TRUE : Enable this entry
- FALSE : Disable this entry
Comment
For documentation, and future references, explainthe relevance of this entry with your policies.
Profiles
Specify the Profiles applicable for this entry.
This entry will be applicable only if the connection has any one of the specified profiles.
Leave it Blank, to apply for all connections irrespective of any applied profile.
To avoid application to a connection that has a profile, use negated profile (!profile).
Type
A regular expression matching the header type to which this entry applies to.
Headers are in the form of type and value.
Leave blank to Match everything.
Example: X-GoogApps-Allowed-Domains.
Value
A regular expression matching the header value's this entry applies to leave blank to match everything.
Leave blank to Match everything.
Example: text/html.
Applies to
This option is to select whether this entry applies to the server header, client header, or both.
- CLIENT : This entry will be applied only for request headers, sent by the client.
- SERVER : This entry will be applied only for response headers, sent by the server.
Insert
In this sub section you can add the rules to modify the request and response headers.
You can insert additional information in the headers sent by your browser.
Enabled
Enable or Disable this entry
- TRUE : Enable this entry
- FALSE : Disable this entry
Comment
For documentation, and future references, explainthe relevance of this entry with your policies.
Profiles
Specify the Profiles applicable for this entry.
This entry will be applicable only if the connection has any one of the specified profiles.
Leave it Blank, to apply for all connections irrespective of any applied profile.
To avoid application to a connection that has a profile, use negated profile (!profile).
Type
A regular expression matching the header type to which this entry applies to.
Headers are in the form of type and value.
Leave blank to Match everything.
Example: X-GoogApps-Allowed-Domains.
Value
A regular expression matching the header value's this entry applies to leave blank to match everything.
Leave blank to Match everything.
Example: text/html.
Applies to
This option is to select whether this entry applies to the server header, client header, or both.
- CLIENT : This entry will be applied only for request headers, sent by the client.
- SERVER : This entry will be applied only for response headers, sent by the server.
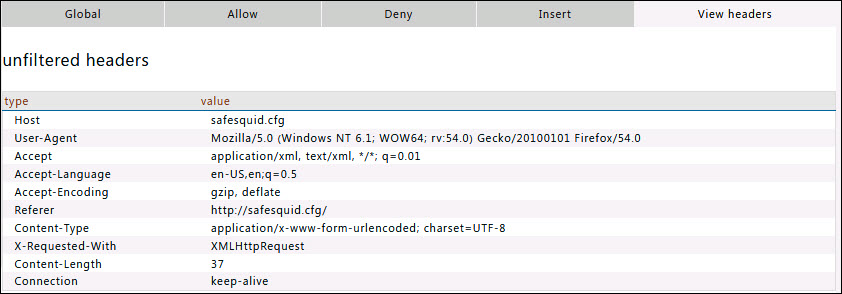
View headers
In this sub section you can find the example headers with type and values.