Difference between revisions of "Network settings"
| (One intermediate revision by the same user not shown) | |||
| Line 65: | Line 65: | ||
=== Example === | === Example === | ||
Rule#1 | '''Rule#1''' | ||
My SafeSquid proxy is running on a cloud server, I use ssh tunnel using 127.0.0.1:8080 to access my proxy server. | My SafeSquid proxy is running on a cloud server, I use ssh tunnel using 127.0.0.1:8080 to access my proxy server. | ||
| Line 76: | Line 76: | ||
[[File:Slide1-NetSet.png|left]] | [[File:Slide1-NetSet.png|left]] | ||
Rule#2 | '''Rule#2''' | ||
I want to use SafeSquid without configuring it in my browser. (As a transparent proxy server) | I want to use SafeSquid without configuring it in my browser. (As a transparent proxy server) | ||
| Line 89: | Line 89: | ||
[[File:Slide2-NetSet.png|left]] | [[File:Slide2-NetSet.png|left]] | ||
Rule#3 | '''Rule#3''' | ||
I want our admin users to access SafeSquid web interface without authentication. | I want our admin users to access SafeSquid web interface without authentication. | ||
Latest revision as of 19:37, 4 January 2023
Overview
Configure the basic Network Infrastructure.
Configure the Sockets on which SafeSquid will Listen, and accept connections from clients.
Manage SafeSquid's outgoing connections through existing IP's of your host system.
Listen
Setup SafeSquid’s Listen Interfaces to accept connections from clients.
When SafeSquid starts-up, all the enabled entries will be evaluated, and create appropriate Listening Sockets.
You may specify these Interfaces when creating policies in Access Restrictions Section.
Evaluation logically skips disabled Entries.
Service restart is required to effect any changes made here.

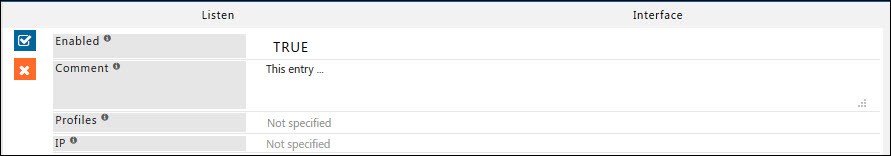
Enabled
Enable or Disable this entry
- TRUE : Enable this entry.
- FALSE : Disable this entry
Comment
For documentation, and future references, explain the relevance of this entry with your policies.
That is, by reading the policies, a future user can understand the purpose of that entry.
Port
Specify the Listen port. By default, SafeSquid listens on port 8080.
Port value can be a positive integer between 1 and 65535. Default value is 8080
IP
Specify the IP address to complete the socket definition.
You may choose a specific IPv4 or IPv6 address.
Empty or Blank: All the IPv4 and IPv6 addresses of the host.
- set to 0.0.0.0 : Listen to all IPv4 IPs only
- set to :: : Listen to all IPv6 IPs only
Bindings
Choose additional bindings (roles) for this Socket.
You may select multiple options if you need.
- SSL_TRANSPARENT : Accept SSL requests in a transparent proxy mode.
- CAPTIVE_PORTAL : Setup a captive portal for user authentication, when SafeSquid is used as a Transparent Proxy.
- SSL_AUTHENTICATION : User authentication via SSL client certificates.(Not Yet Implemented)
- SSL_BRIDGE : If SafeSquid has been setup as Reverse Proxy, and must provide SSL for non-SSL HTTP servers.(Not Yet Implemented)
Example
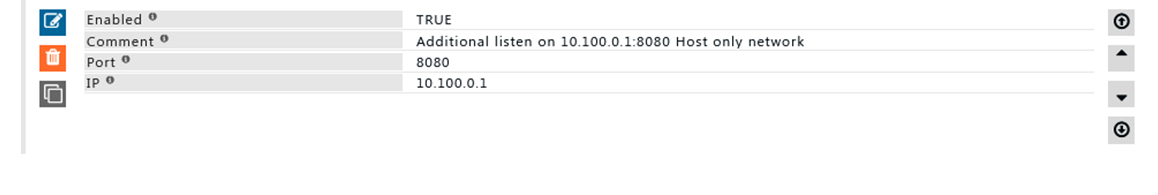
Rule#1
My SafeSquid proxy is running on a cloud server, I use ssh tunnel using 127.0.0.1:8080 to access my proxy server.
I have host only network with IP range 10.100.0.0/16
I want my proxy server to listen on 10.100.0.1:8080
Using the network -> listen policy we can allow proxy to listen to addition IP and ports.
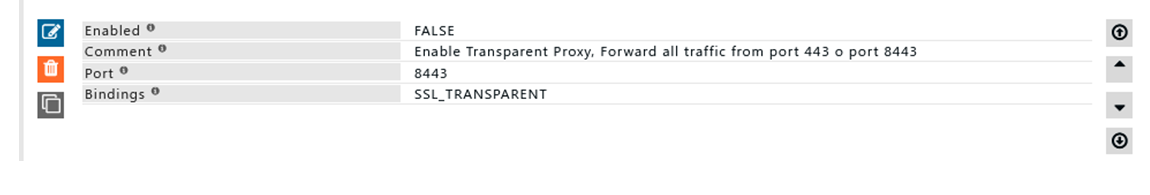
Rule#2
I want to use SafeSquid without configuring it in my browser. (As a transparent proxy server)
I want to transfer all traffic from port 80 to be forwarded to port 8080 and traffic from 443 to be forwarded to 8443.
I want SafeSquid to listen to port 8443
Rule #2 is configured to use proxy server as a transparent proxy server.
Bindings set as SSL_TRANSPARENT is used to accept SSL request in transparent mode.
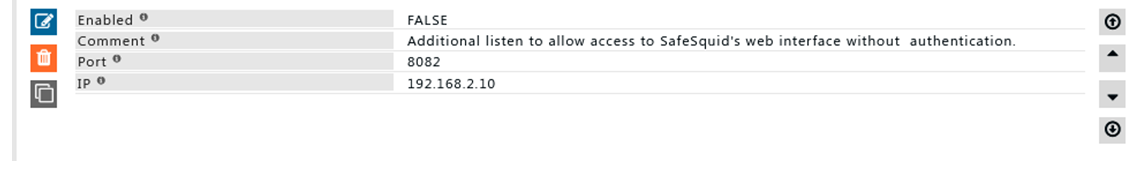
Rule#3
I want our admin users to access SafeSquid web interface without authentication.
General users’ access internet using port 8080 where GUI access is disabled.
We want SafeSquid to listen on IP 192.168.2.10 and port 8082 which has access to SafeSquid web interface, can be configured in “Access Restrictions”.
Rule #3 can be used where user identification is not performed and personal having access to SafeSquid’s web interface should be limited.
Interface
Specify Interfaces for outgoing connections.
SafeSquid can take advantage of multiple ISPs or outbound connection routes, on multi-homed host systems.
Create multiple entries as required.
SafeSquid evaluates all enabled entries starting from top, and selects the first one that matches the connection.
Evaluation skips the disabled Entries.
Enabled
Enable or Disable this entry
- TRUE : Enable this entry.
- FALSE : Disable this entry.
Comment
For documentation, and future references, explain the relevance of this entry with your policies.
That is, by reading the policies, a future user can understand the purpose of that entry.
Profiles
Specify the Profiles applicable for this entry.
This entry will be applicable only if the connection has any one of the specified profiles.
Leave it Blank, to apply for all connections irrespective of any applied profile.
To avoid application to a connection that has a profile, use negated profile (!profile).
IP
Specify an IP address assigned to the host system.
SafeSquid will bind the outgoing connection to this IP address thus effectively applying the desired routing for the connection.
Note : The configuration must be saved and the proxy server has to be restarted before any changes take effect.
Example
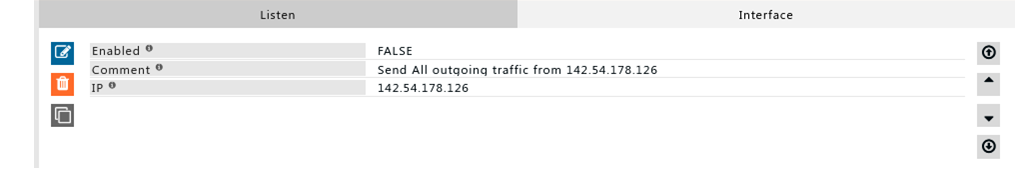
Rule#1
I want to send all my outgoing traffic via a different route than incoming traffic.
142.54.178.126 is used as outgoing traffic
Using multiple ISP’s provide redundancy. Enhance throughput.
Rule#1 can be used to configure multi homed network.
See Also
Secure WIFI Access Through Active Directory Infrastructure And SafeSquid Captive Portal