Application not working with HTTPS inspection
Business challenge
The HTTPS inspection Bypass option enables you to define specific websites that are not subject to decryption as they flow through the proxy. Some websites may include personal identification information that should not be decrypt. In order to avoid liability for inspecting this type of information, you may want to specify some or all of these sites for decryption bypass. The selected sites will not be decrypt even if the category or categories that the sites belong to are selected for SSL analysis.
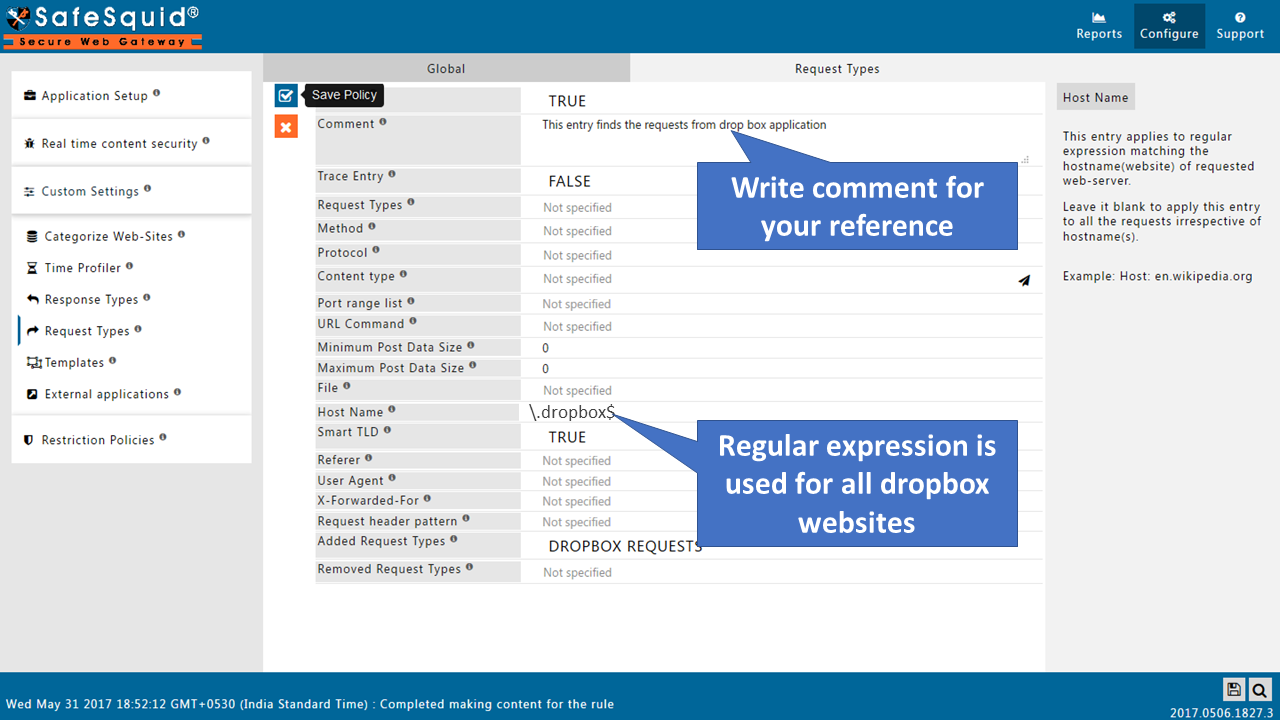
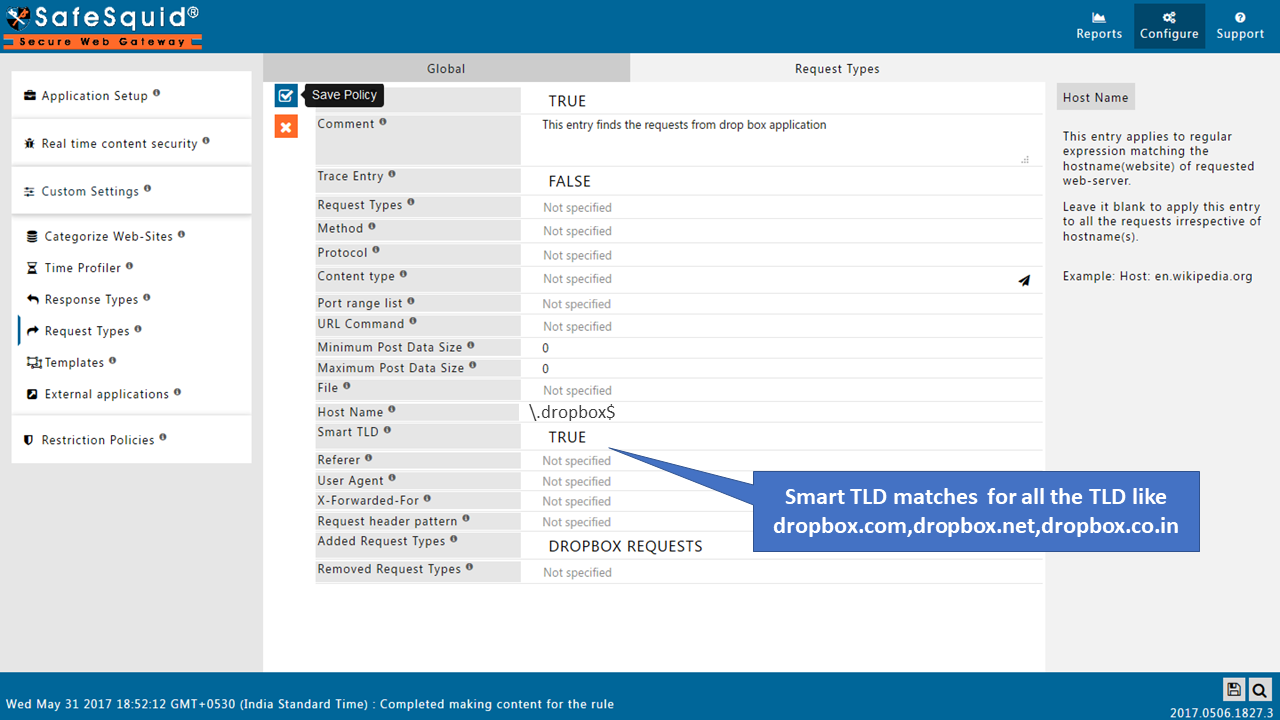
Note : Tunneling application is the group of applications which is specially made for bypassing applications which are not working with HTTPS inspection.We have list of some default applications if any application which is not included in Tunneling application, that application you have to select manually from magic suggest.
Here will give you an example of how to bypass an application which is not working with HTTPS inspection.
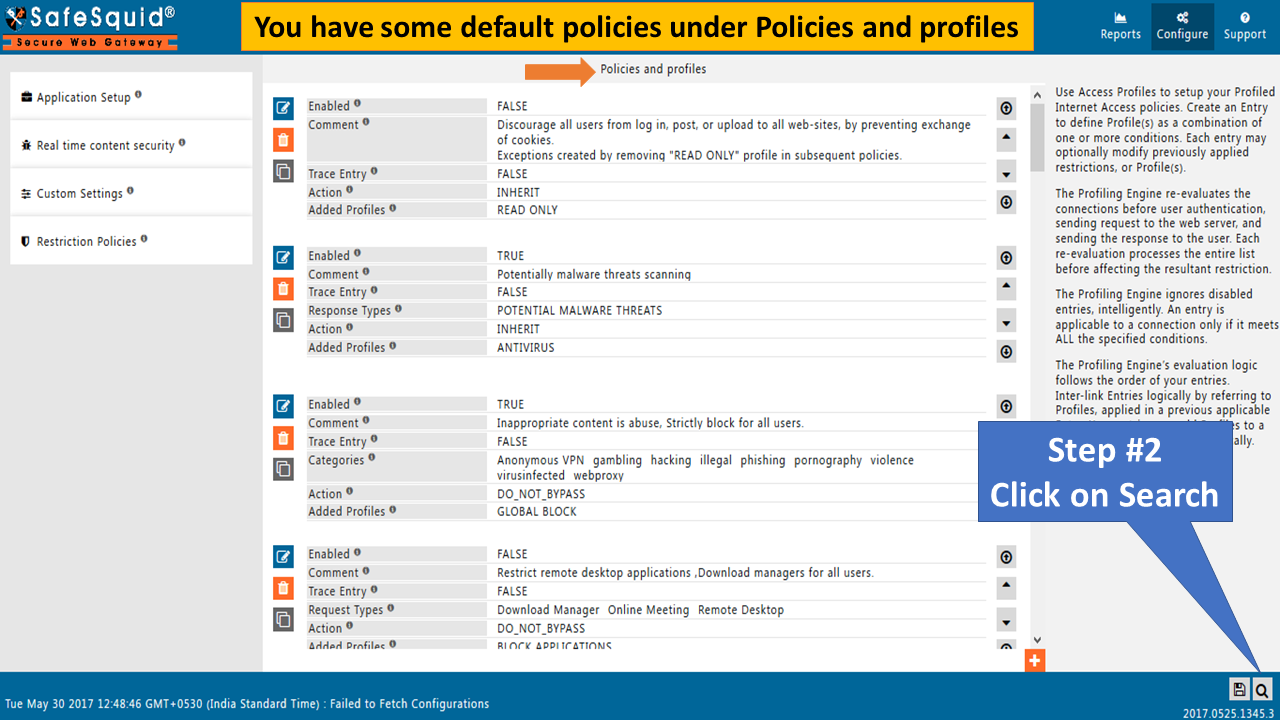
To bypass HTTPS Inspection enabled SafeSquid default configuration
Access the SafeSquid User Interface
 |
|
|
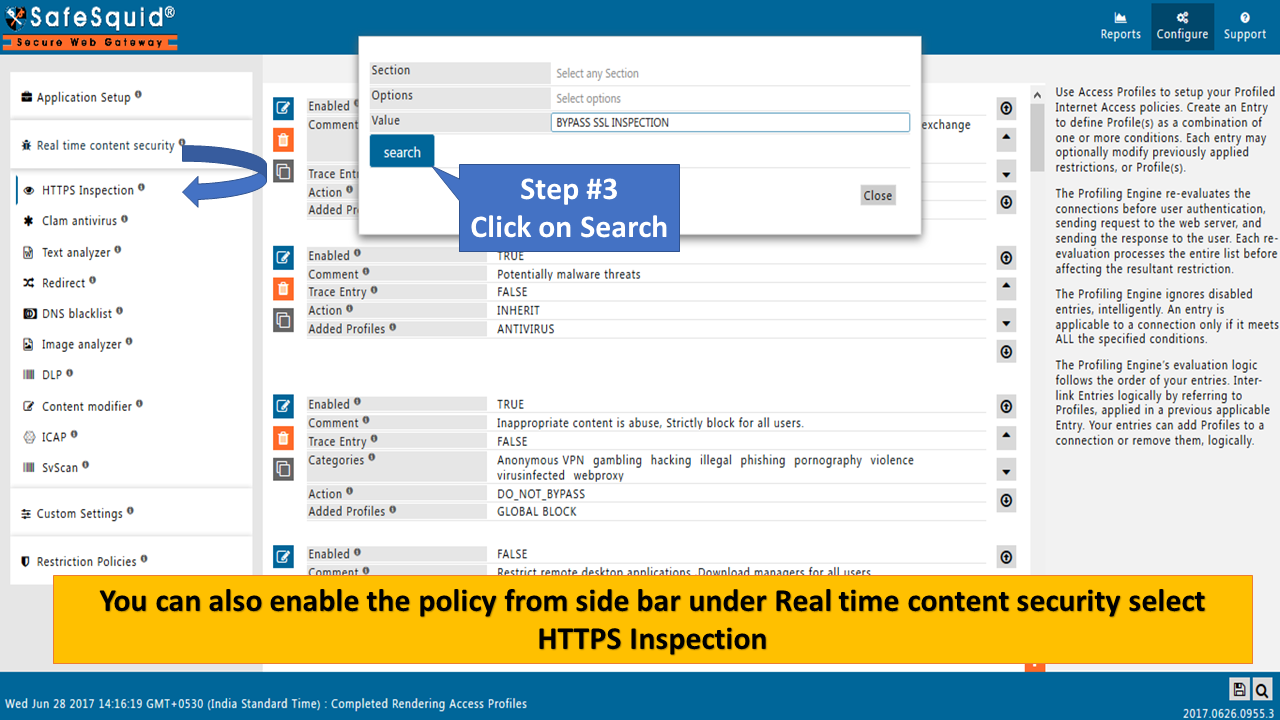
Search policy : "BYPASS SSL INSPECTION" to Search |
|
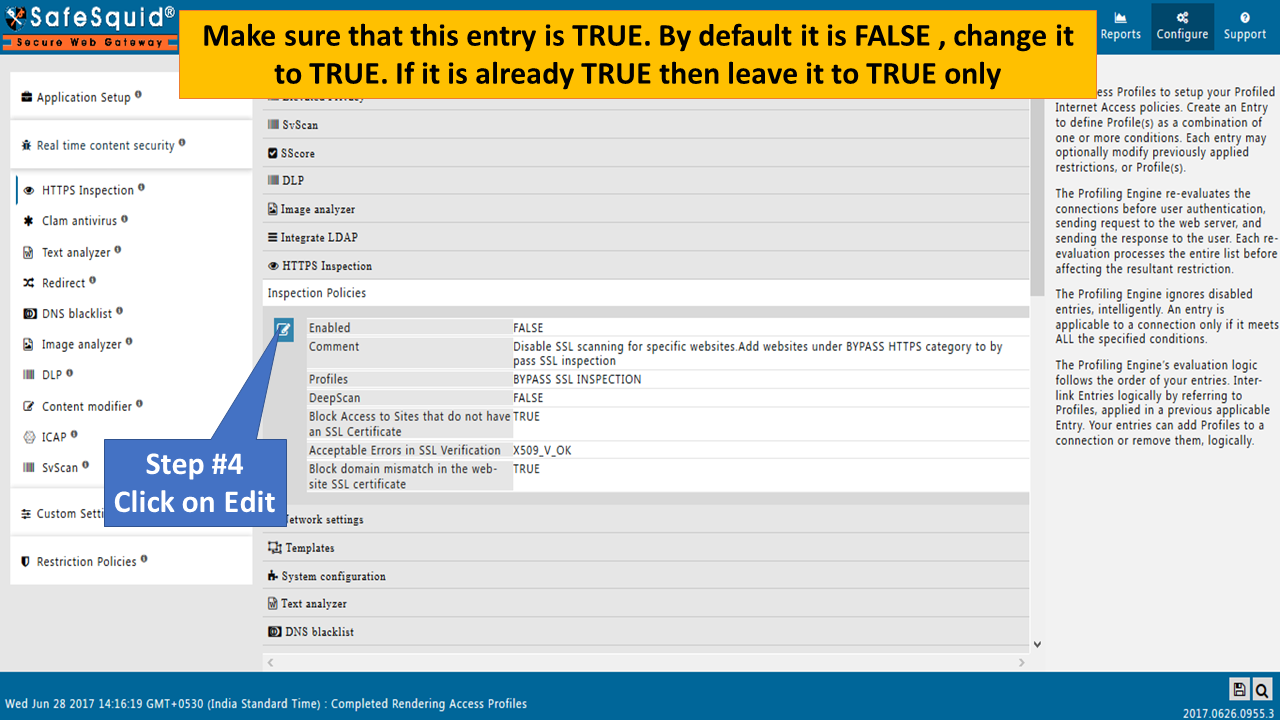
Edit policy to Enable as TRUE (Inspection Policies) |
|
 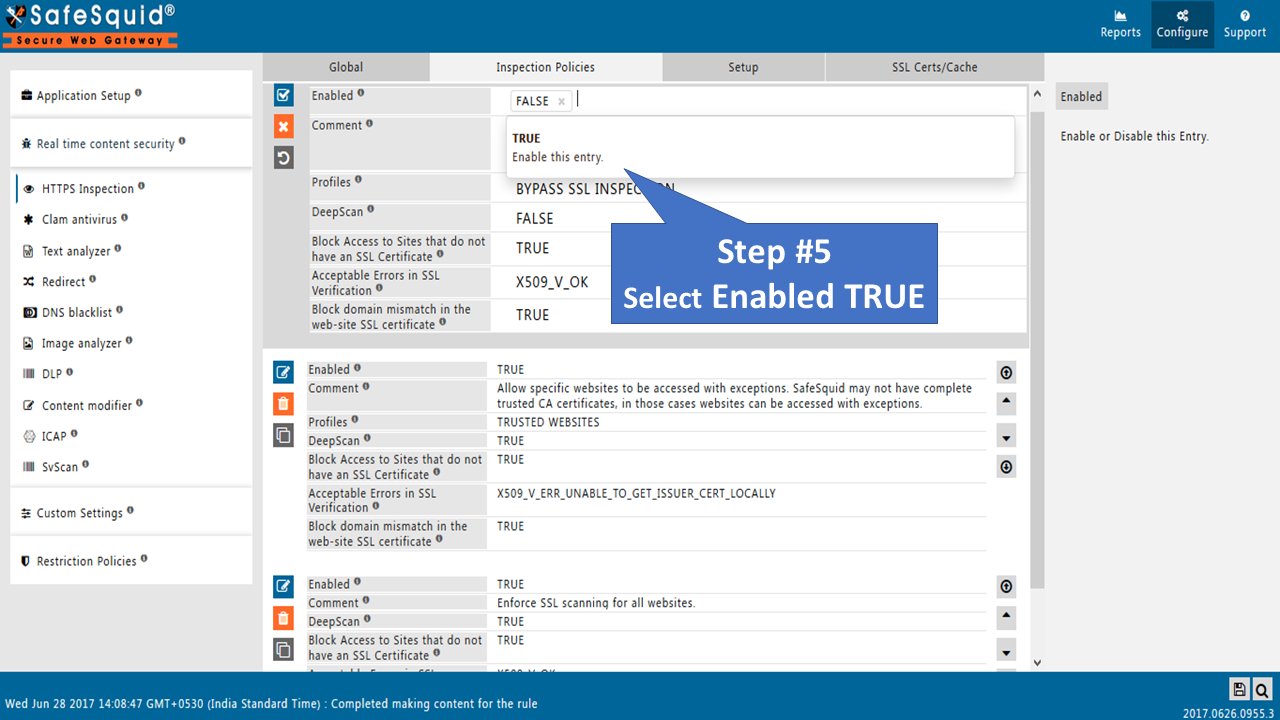 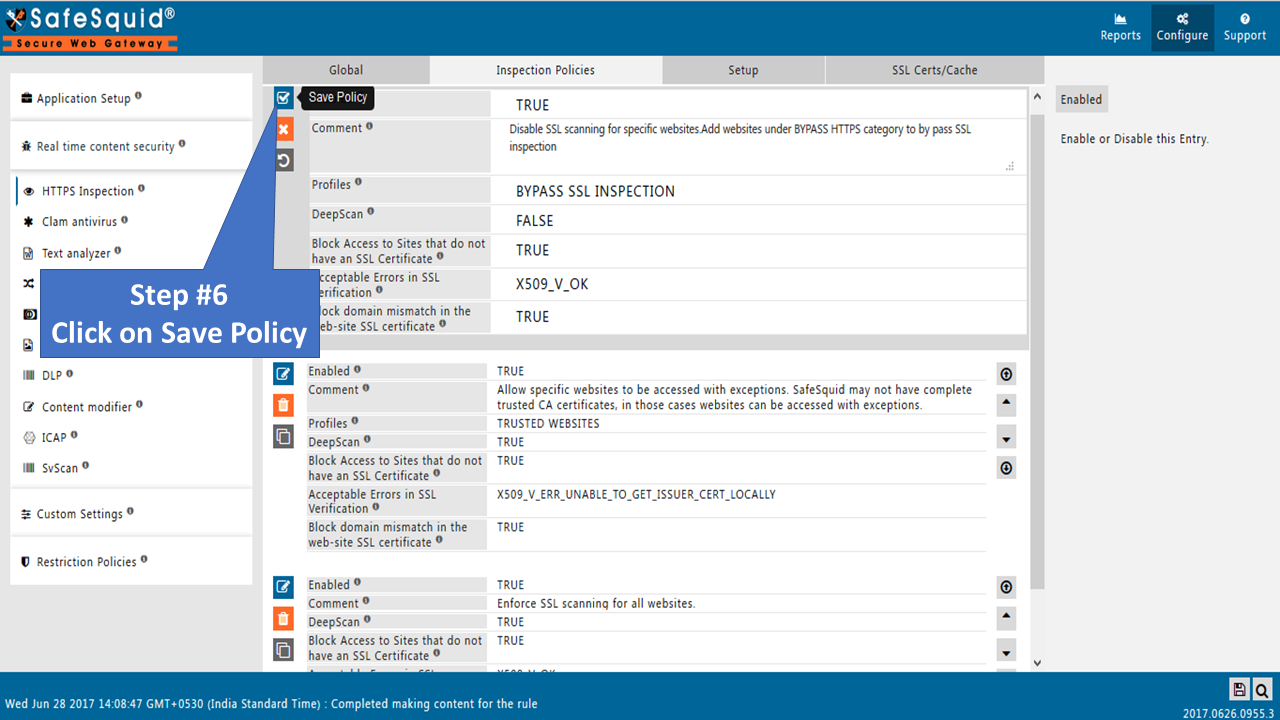
Edit policies and profiles to Enable as TRUE |
|
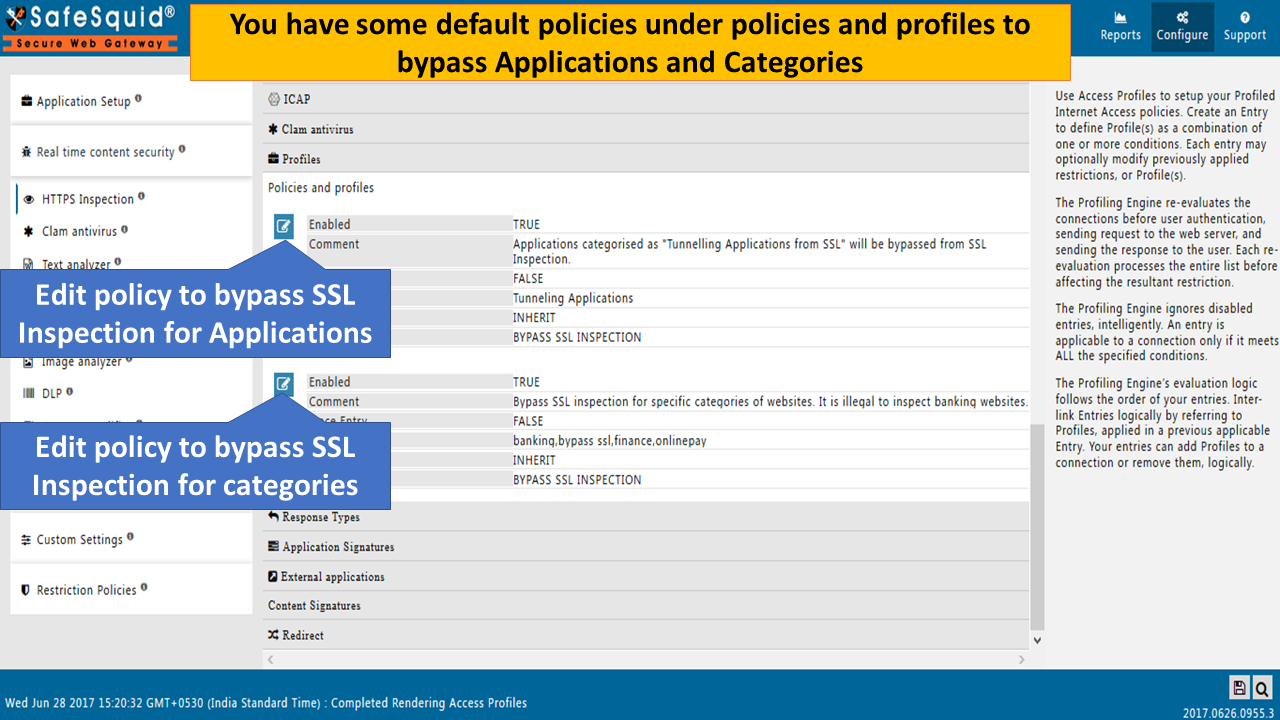
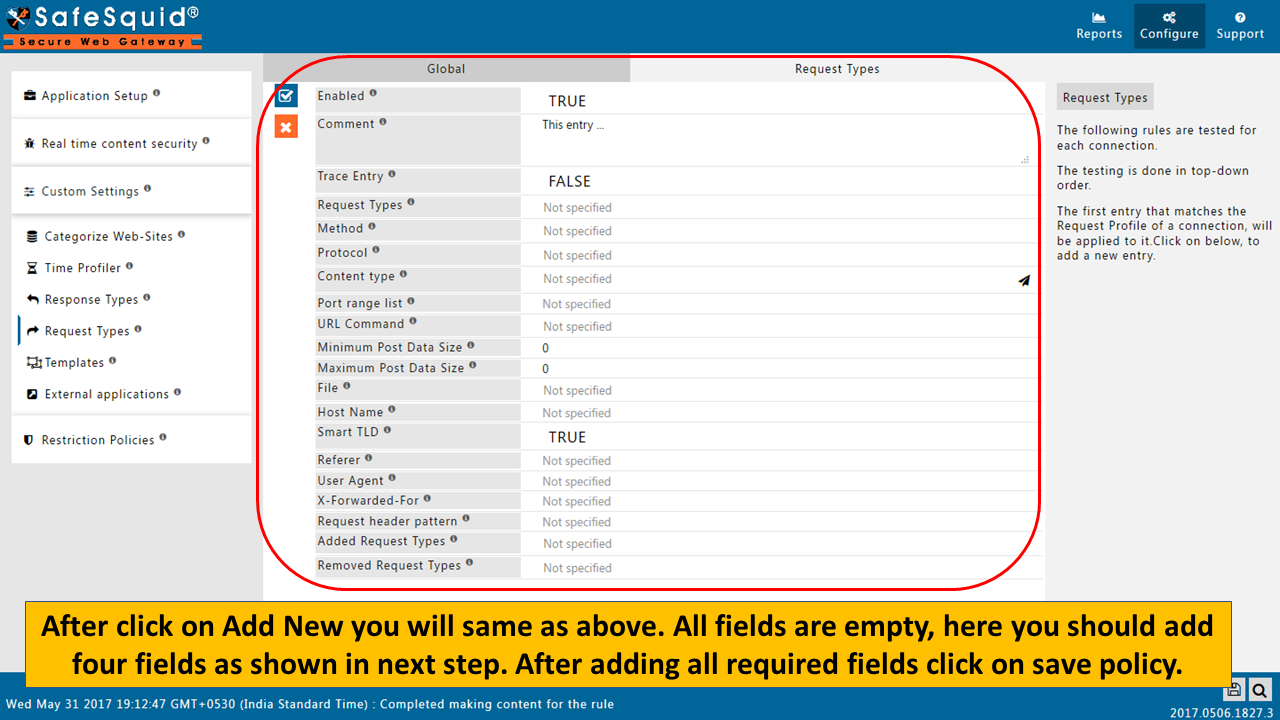
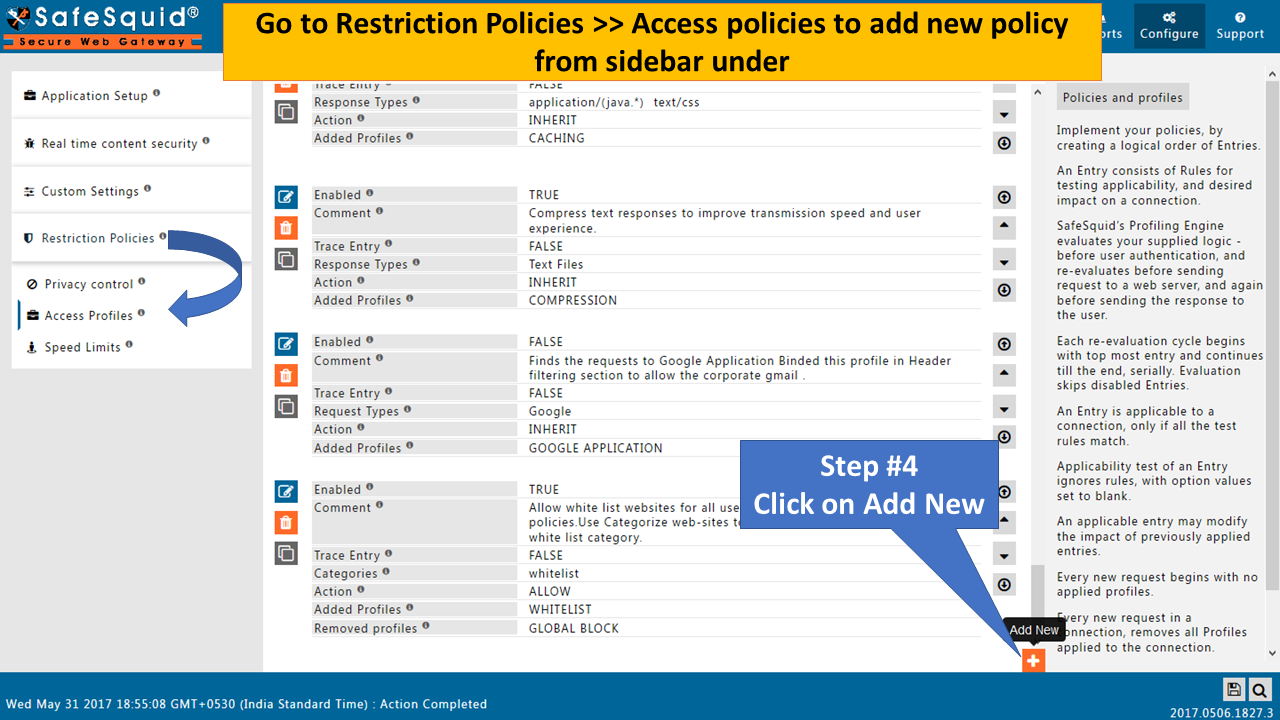
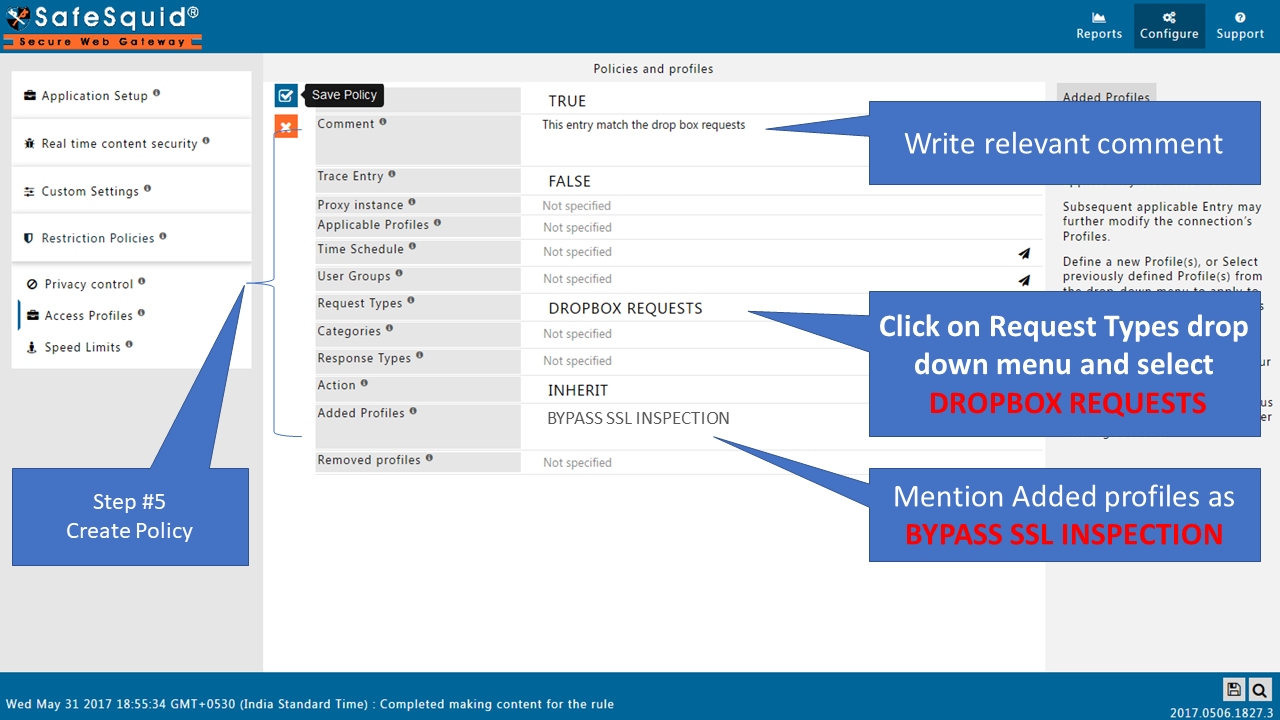
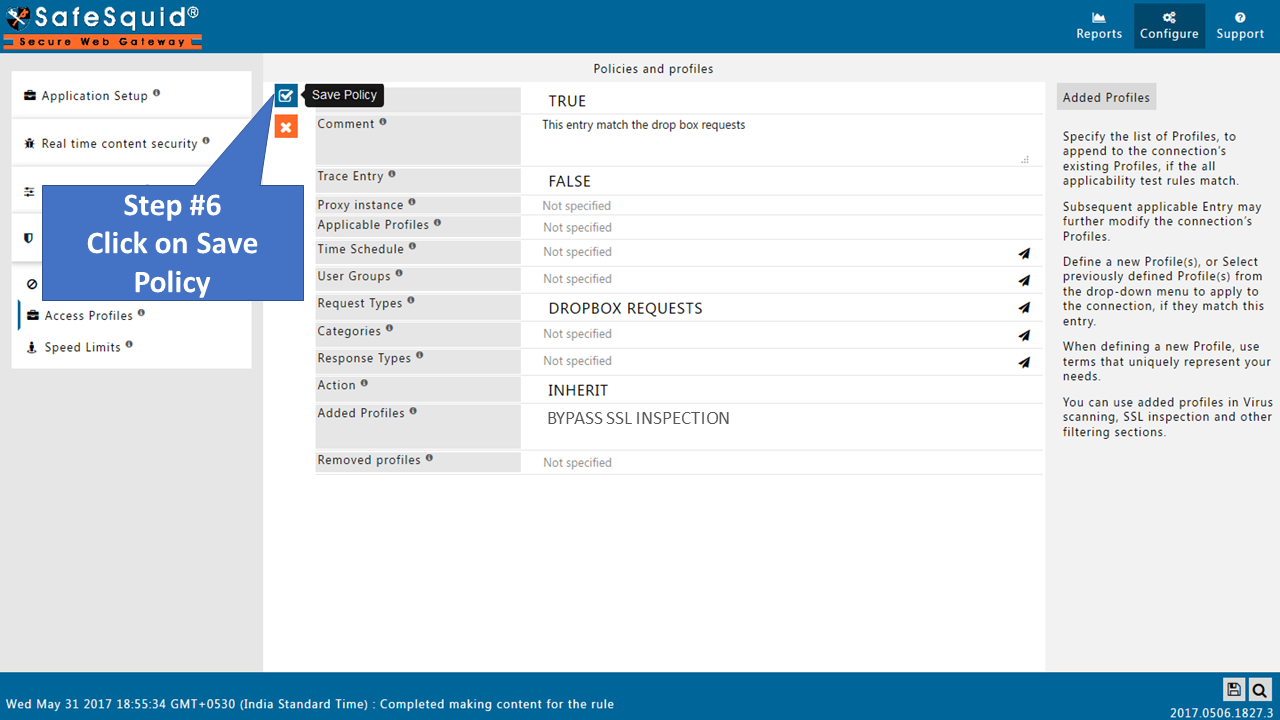
How to create new policy to bypass HTTPS Inspection |
|
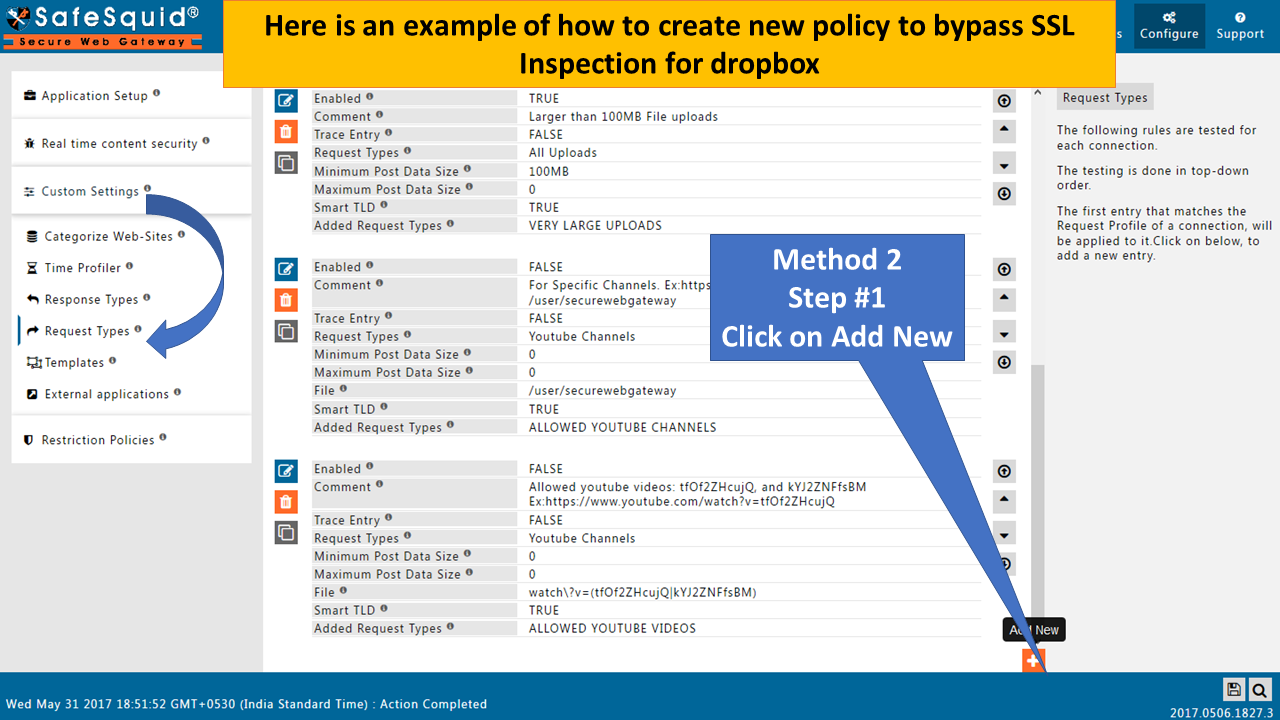
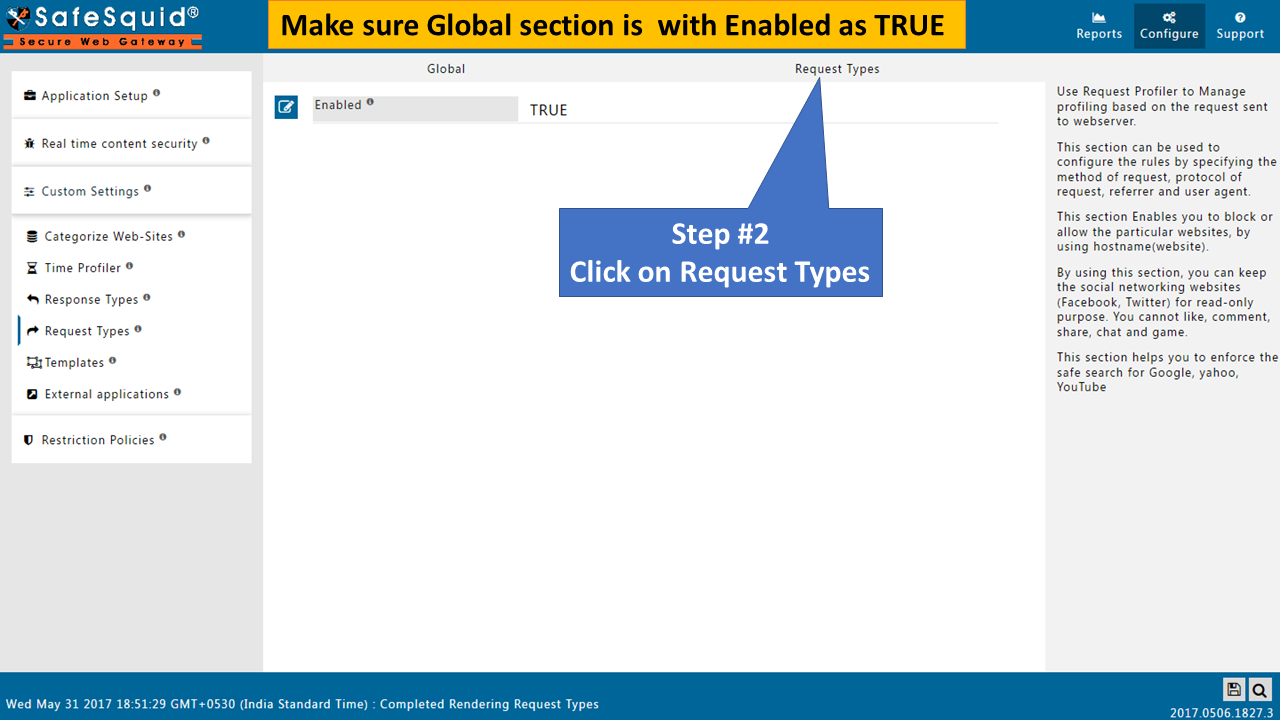
Go to Request Types |
|
 |
|
 |
|
 |
|
 |
|
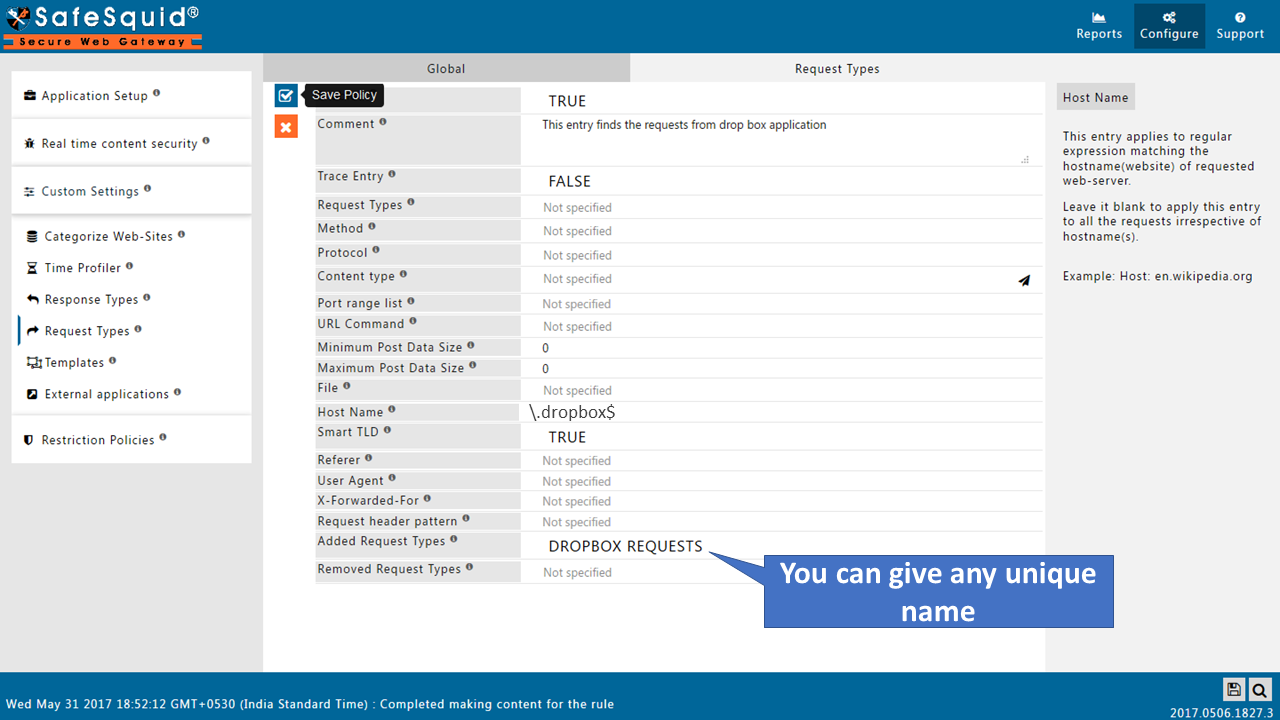
Go to Access Policies |
|
 |
|
 |
|
 |
Note: Configure Proxy settings in drop box and upload/download files to validate the working