Difference between revisions of "Defend Against Internal Threats And Data Leakage"
en>Santosh.thorat |
m (1 revision imported) |
(No difference)
| |
Latest revision as of 00:31, 25 July 2021
Overview
According to a recent survey of hundreds of IT security professionals, most organizations have major security holes when it comes to protecting themselves against insider threats. Not all data loss is the result of external, malicious attacks. The inadvertent disclosure or mishandling of confidential data by internal employees is also a significant factor. If your IT security isn’t in place across all devices that employees use then it’s an open invitation to hackers and fraudsters. Organizations overwhelmingly maintained that the data loss was the top concern regarding insider threats. When asked which types of insider attacks were most concerned, 63 percent of respondents said data leaks, 57 percent said inadvertent data breaches and 53 percent said malicious data breaches. In these days, the role that insiders play in the vulnerability of all sizes of corporations is massive and growing.
So, who are these insiders?
Some are individuals who have malicious intent to cause harm or embarrassment to their companies or governments and others are just inattentive, bored, or complacent employees with no malicious intent at all.
What includes internal attacks?
- Data leakage
- Intellectual property theft
- Data corruption and/or loss
With the goal of mitigating all types and levels of insider threat, the SafeSquid delivers advanced security and risk-management solutions.
SafeSquid’s DLP module is the key solution to the Data Leakage. Using DLP module of SafeSquid can restrict the users to download or upload specific type of files, and also in memory virus scanners like SvScan prevents the all users from downloading and uploading virus infected files. By providing role based access to the users, keep your organization safe and secure from internal attacks.
Key solutions provided by SafeSquid
Data Loss prevention
Data loss prevention (DLP) is a strategy for making sure that end users do not send sensitive or critical information outside the corporate network. The term is also used to describe software products that help a network administrator control what data end users can transfer. A recent study towards data leakage said that internal data leakage is much more serious than external data leakage. The insider threat can be particularly difficult to guard, if someone is using their legitimate access to data for perverse purposes. DLP can detect files that contain confidential information and prevent them from leaving via the network.
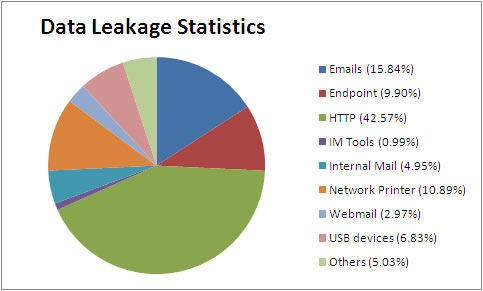
Below are the general statistics regarding Data Leakage
In memory Virus scanning
All over the world there are numerous ways to protect and remove malware from your computers. The key pathway through which malware attacks the system is the Internet and its popular service, the Web. Not a single method is enough to ensure your computer is secure. The more layers of defense, the harder for hackers to hack your computer.
You can integrate different types of Virus scanners in ICAP module. By default SafeSquid comes with Svscan virus engine, it will block all uploads and downloads of all types of files.
Role based access
With hundreds and thousands of users on your network, it can be overwhelming to try and provision everyone with the correct access in a timely fashion. Allowing full access to all users resulting in a backlog of requests, a long wait for access, great loss in bandwidth and too often unnecessary access rights being granted leaving you vulnerable to a breach.
Rather than dealing with these headaches, you could handle provisioning by role-based access by using SafeSquid easily.
By using SafeSquid you can restrict the users access based on their roles. You can integrate any centralized system for your users management with SafeSquid.
Real-Time Monitoring
With real-time monitoring, like SafeSquid Reporting Module, you can see into your system at any time as well as be alerted when things look wrong.
For example, if four new users were granted access to a critical application in one week in your network, would you like to notice?
With real-time monitoring you would be alerted to such type of event so that you can investigate and mitigate the risk of a breach.